The WordPress Import XML and RSS Feeds plugins have two significant vulnerabilities that can allow hackers to install web shells and deploy malware on targeted systems, putting over 3000 servers worldwide at risk. Attackers can use Living off the Land Binaries malware to execute commands and access files, leading to data exfiltration, credential theft, ransomware, denial of service, crypto mining, and botnet activities. The Virsec Security Platform can safeguard servers against these attacks, making it a proactive compensating control that offers server protection, even when an organization cannot apply software patches promptly.
Background: Over 3000 servers worldwide actively use the WordPress Import XML and RSS Feeds plugin. On September 25th, 2023, the US-CERT’s National Vulnerability Database (NVD) identified two vulnerabilities, CVE-2023-4300 (High Impact) and CVE-2023-4521, in versions 2.1.4 and below of this plugin.
Exploitation Risk: These vulnerabilities can allow a malicious actor to install a web shell and deploy malware on targeted systems. Depending on the attacker’s objectives, this malware can propagate within the network and initiate various attacks, including data exfiltration, credential theft, ransomware, denial of service, crypto mining, and botnet activities.
In-Depth Analysis: On August 28th, 2023, a researcher named Jonatas Souza Villa Flor discovered that the plugin fails to filter file extensions for uploaded files, enabling attackers to upload malicious PHP files, and resulting in remote code execution. The WordPress Security Scanner provided a proof-of-concept code that establishes a persistent command shell for the attacker’s control, facilitating further malware deployment.
Advanced Threat Techniques: Sophisticated attackers can use LOLBin (Living off the Land Binaries) malware instead of easily detectable executable malware. LOLBin malware leverages OS runtime utilities like bash and awk to execute commands, manipulate permissions, gather process information, extract credentials, access SSH private keys and known_hosts files, encode and encrypt data, inspect bash history, and even remove itself.
Kill Chain: We can divide the attacker’s activities into five stages: reconnaissance, persistence, weaponization, exploitation, and exfiltration:
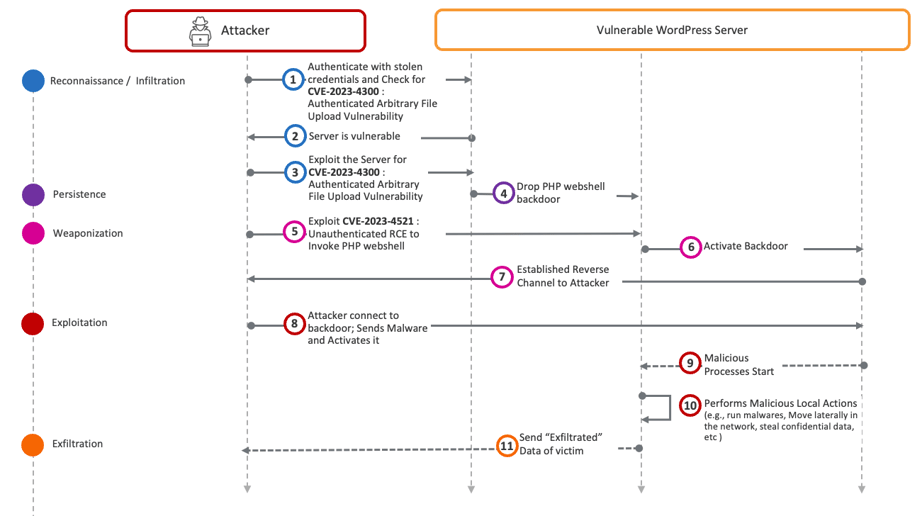
During the reconnaissance stage, Threat Actors leverage tools like Shodan to locate potentially vulnerable servers. Once found, the attacker verifies if the target uses the vulnerable WordPress plugin. Subsequently, in the persistence stage, the attacker establishes a reverse channel for control. In the weaponization stage, the attacker deploys the appropriate malware (such as LOLBIN scripts) for further reconnaissance, lateral movement, and data exfiltration. In the exploitation stage, the attacker performs malicious actions like lateral movement and data theft. Finally, in the exfiltration stage, critical data is sent back to the Threat Actor’s command and control center.
Virsec Security Platform (VSP) Protection: VSP is crucial in this scenario, as it identifies, within milliseconds, any code executed by the attacker during the reconnaissance stage as influenced by the attacker.
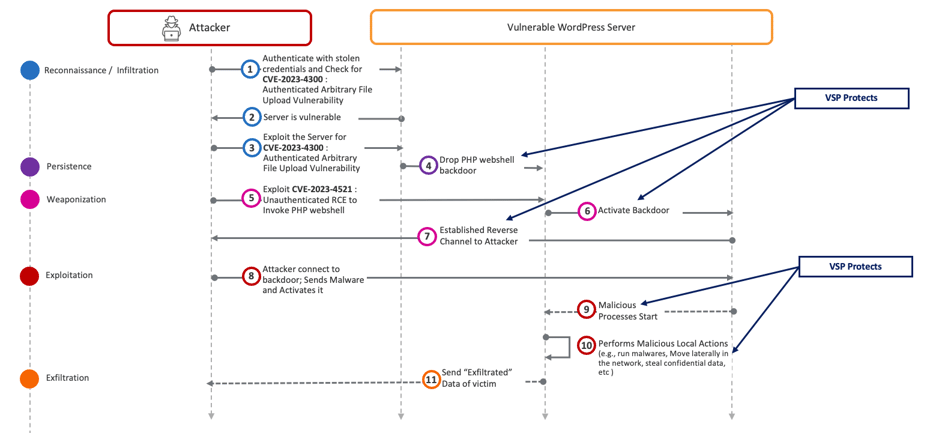
Even before the malicious code runs at Step 4, VSP’s Application Control Engine recognizes that no legitimate application is authorized to perform such actions. As a result, VSP safeguards the victim server by taking protective measures, such as terminating the user’s session, restarting the WordPress server, or closing the network socket used for communication with the attacker’s control center.
Demonstration: Watch a video illustrating how Virsec VSP thwarted Threat Actors that targeted these vulnerabilities at https://youtu.be/TrV5-9lq03c.
Key Takeaways:
-
Organizations must respond promptly when information on Remote Code Execution vulnerabilities in deployed software becomes known. Threat actors are a constant threat, and the question isn’t if they will attack but when.
-
While WPScan reported the vulnerability on August 28th, 2023, it’s challenging to determine if Threat Actors used these vulnerabilities even earlier.
-
The Virsec Security Platform (VSP) provides proactive compensating controls, safeguarding systems even when patches cannot be applied promptly. CISOs can trust VSP to protect their systems.
For more information about the Virsec Security Platform (VSP) and how we protect vulnerable legacy workloads, visit www.virsec.com.
Don't miss our security insights, and subscribe to our blog now.