Read our latest press release announcing the launch of our newest products - TrustSight and TrustGuardian
Virsec’s new generation runtime defense platform is purpose-built to protect server workloads from ransomware and other sophisticated attacks by providing clear visibility into what’s running on them, verifying provenance, creating trust policies, and blocking any deviations in milliseconds. Virsec’s default-deny, allow-on-trust solution significantly contributes to an overall zero trust strategy. This allows organizations to balance risk tolerance with business continuity as they face the challenge of adapting to ever-expanding attack surfaces.

The Virsec Security Platform (VSP) ensures system integrity by verifying the trustworthiness of all libraries, processes, scripts, and executables. Once trust is established, VSP enforces trusted runtime execution, which stops malicious code in milliseconds. Using a default-deny, allow-on-trust approach, VSP prevents cyber attackers from exploiting vulnerabilities in both modern and legacy application workloads and stops ransomware, novel, zero-day, RCE, LOLBin, and malware attacks.

Virsec’s TrustSight is a new tool that combines three essential elements for the clearest view yet into your attack surface environment
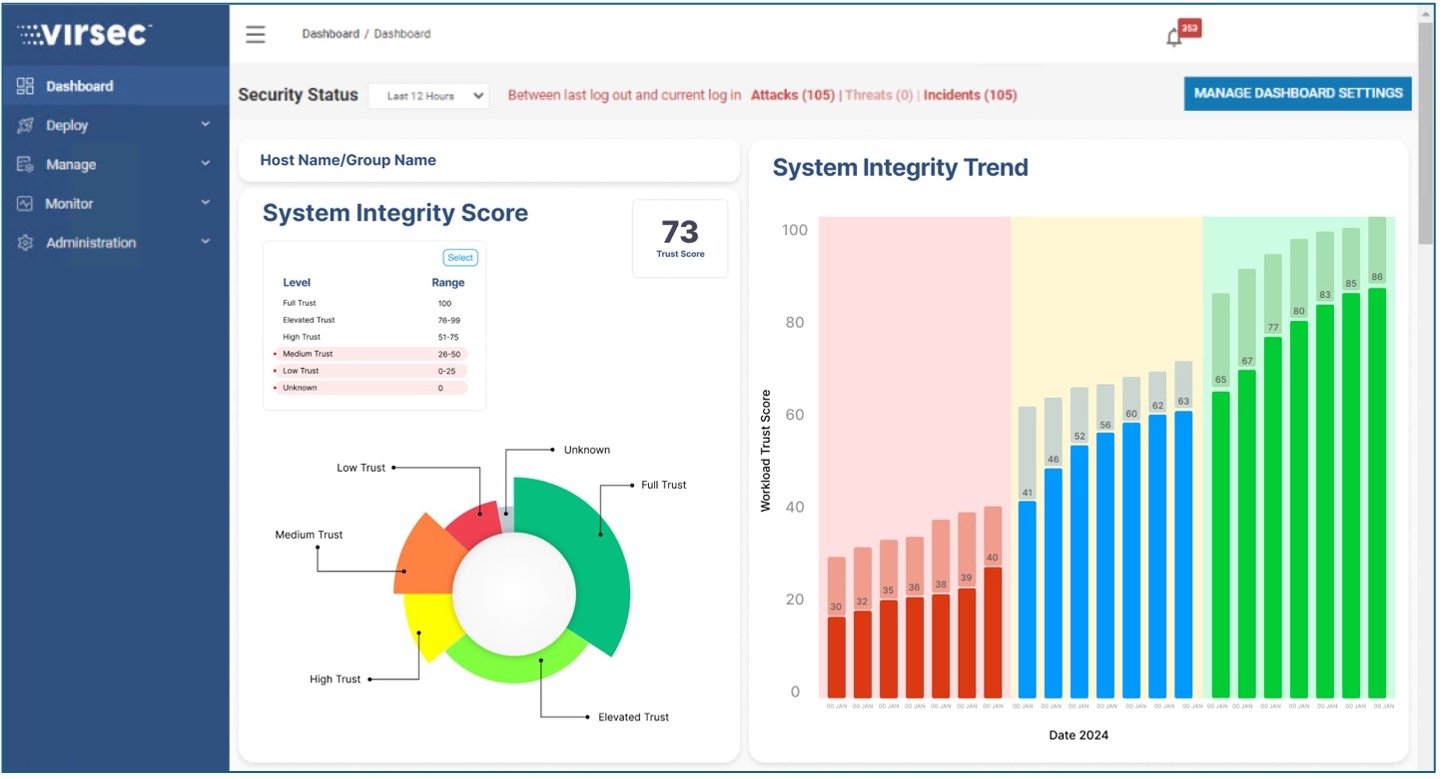
Organizations can’t protect what they can’t see and understand. Asset visibility is a crucial first step for a zero trust strategy, and Virsec’s TrustSightProvides dynamic visibility in runtime into all processes, executables, libraries, and scripts running on server workloads.
This precise, fine-tuned telemetry source is a critical component that provides the comprehensive insight and context required to manage the workload attack surface by assessing the current level of vulnerability and risk.
TrustSight provides system integrity by automatically analyzing all processes, executables, and scripts running on the server workload and establishing provenance (trusted publisher certificate, windows SFC signature, ISV provenance, customer repo provenance, trusted compiler provenance) and file reputation to create a trust score.
With this observability, TrustSight creates baselines that serve as the basis for creating trust policies. This ensures that the server workload performs its intended function without unauthorized manipulation, whether intentional or accidental.
TrustSight is an advanced tool that monitors the behavior of server workloads in runtime . It will detect any deviations from established trust policies (e.g., unauthorized memory space being utilized, indicative of an RCE attack compiling data into code) and provide immediate visibility to enable prompt intervention by SOC teams.
TrustSight integrates with leading threat intelligence feeds, SIEM, and SOAR tools, providing high-fidelity alerts of emerging threats and vulnerabilities. This proactive approach keeps the organization ahead of potential attacks, including zero-days.
By enforcing trust policies created by TrustSight, Virsec’s TrustGuardian delivers robust runtime server workload protection, stopping ransomware, zero-days, malware, and other malicious code in milliseconds before it can infiltrate the organization. This default-deny, allow-on-trust approach fills gaps where EDR/XDR solutions fall short.

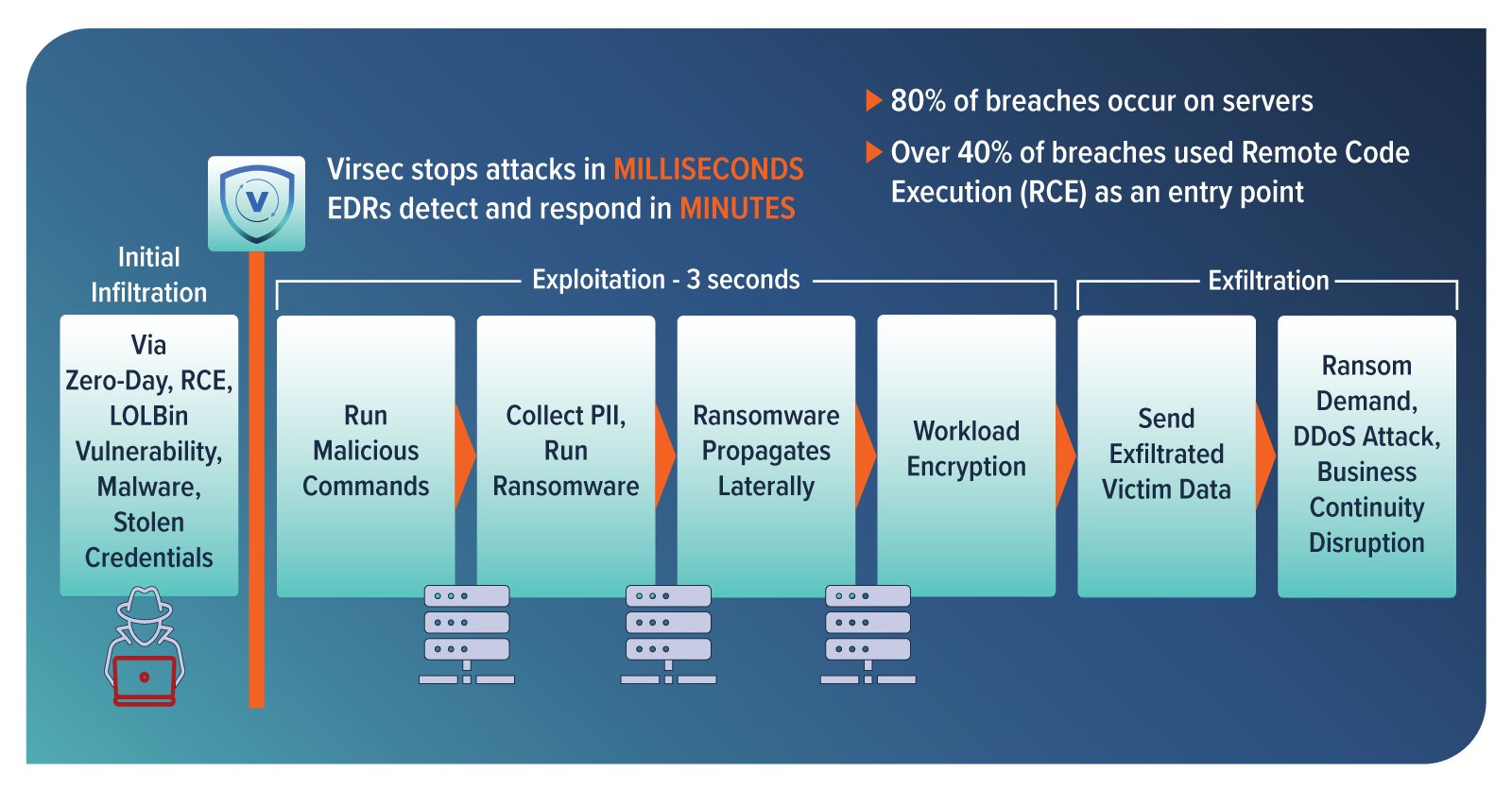
Numerous studies and real-world experiences have revealed that Endpoint Detection and Response (EDR) solutions are not always efficient in detecting a significant portion of known and unknown cyber-attacks. Estimates suggest that 30% to 70% of threats may go undetected, which can vary depending on factors such as the complexity of the attack, the effectiveness of the EDR solution's detection algorithms, and how quickly new threats emerge and evolve. Furthermore, EDRs can take up to 6 minutes to detect an attack, providing cybercriminals with ample time to cause harm.
Virsec offers a more reliable approach that verifies the origin of all code running on server workloads. This ensures that only trustworthy and secure code is executed, even if there are unpatched vulnerabilities. Both known and unknown attacks are stopped in milliseconds, with zero dwell time, making it impossible for attackers to move laterally.
End-of-life (EOL) Legacy Windows and Linux server workloads that are no longer supported pose a substantial security risk because vulnerabilities can’t be patched without expensive extended security options (ESUs). TrustGuardian provides a highly effective compensating control to meet regulatory compliance and harden unpatchable systems for organizations with legacy systems that can't be upgraded or need protection during cloud migration. Attacks are stopped in milliseconds by only allowing trusted, known “good” code to run rather than blocking the known “bad” code.
Software patches only protect against known attacks, leaving server workloads susceptible to zero-day and novel attacks. TrustGuardian provides server workload protection in between patching cycles by enforcing a highly effective compensating control with a default-deny, allow-on-trust approach. This prevents vulnerabilities from being exploited, allowing SOC teams to avoid panic patching.
Compliance is intrinsically tied to security and is complicated. Failure to follow compliance guidelines can increase an organization’s cyber risk. The Virsec Security Platform (VSP) helps ensure regulatory compliance by providing continuous telemetry monitoring, compensating controls, and comprehensive reporting and audit trails, facilitating adherence to industry standards across multiple frameworks, including NIST, HITRUST, PCI DSS, and many others.
System Integrity Assurance
Establish provenance and integrity of executables and libraries used in the workload
Restricts general-purpose apps from performing additional activities not required by the customer's use cases
Updates provenance, integrity, and hardening when code on workloads changes
Reports on privilege infringements at runtime
Generates deep forensics on each cyber incident and facilitates remediation
Provides visibility into what’s running on server workloads and prioritizes identified risks that present the biggest threat to the organization.
Additional telemetry identifies inherent risks that can be countered while mitigating residual risk.
By preemptively detecting and stopping known and unknown security threats in milliseconds, VSP minimizes the risk of downtime and disruption to your business operations, ensuring continuity and productivity.
By reducing the time to identify an incident and stop it to milliseconds, rather than days and weeks, incident response cost is drastically reduced. The shorter the time to find and resolve a breach, the less expensive it is.
The ever-changing threat landscape requires multiple defensive measures to protect an organization’s assets.
VSP provides an additional layer of advanced security to ensure threats are stopped regardless of the infiltration method.
Dynamic visibility and actionable observability empower organizations to establish trust policies based on runtime behavior.
By using this foundation, a zero trust architecture can be achieved, and organizations have confidence that they are building an environment where they are future-proofing against the next cyber-attack vector.
The shortcomings of EDR/XDRs are well known. Security leaders across all industries know that cyber-attacks and ransomware could severely compromise data, affect patient safety, disrupt operations, and potentially cost millions to remediate.
Virsec’s customers repeatedly tell us they have peace of mind knowing their most critical assets running on server workloads are protected, and their organization is more secure.
~ Director of IT / U.S. Critical Infrastructure Organization
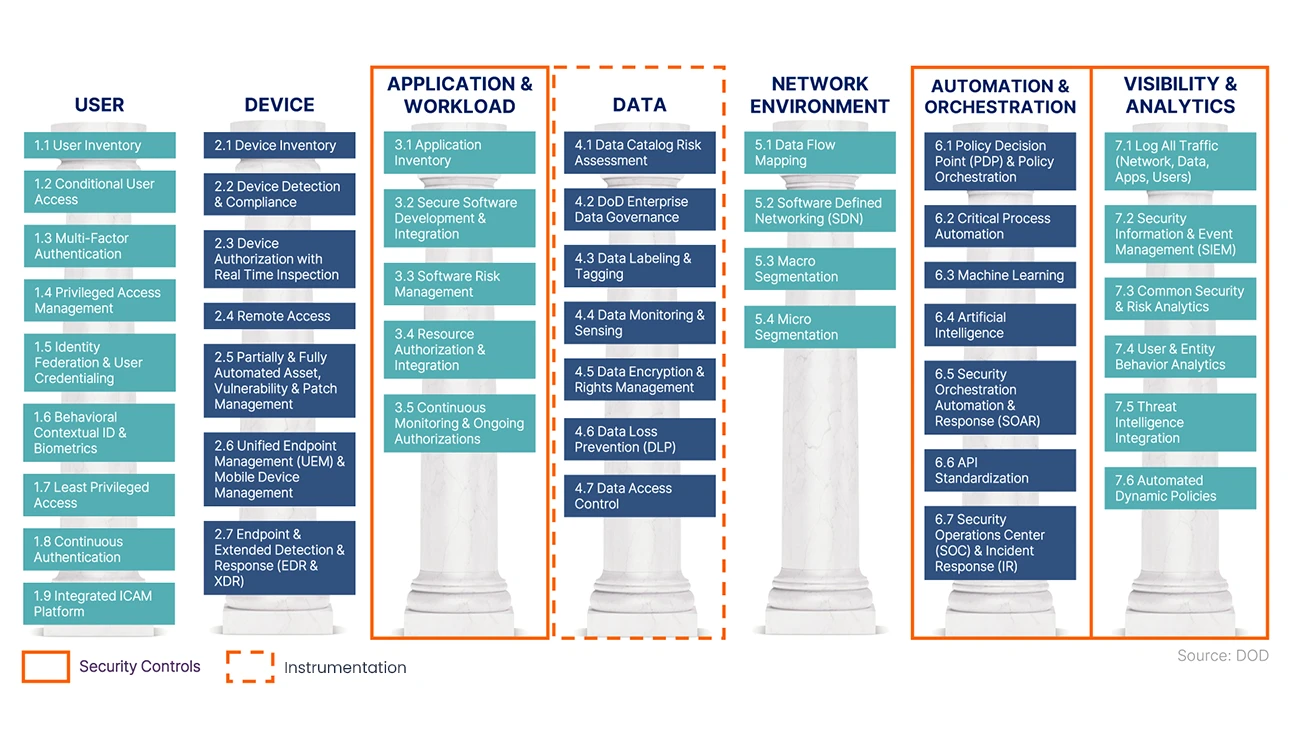
The Virsec Security Platform (VSP) is a security solution that allows your organization to balance risk tolerance with business continuity while building a future-proof security architecture. VSP provides visibility and observability for both modern and legacy workloads, which is crucial to a zero trust strategy. VSP verifies the trustworthiness of server workload components and enforces trusted runtime execution to stop malicious code within milliseconds. By implementing a default-deny policy that allows actions based on trust, VSP effectively safeguards against various cyber threats, including ransomware and zero-day attacks, filling a critical gap in EDR/XDR solutions.