This blog post is a deep-dive analysis of the Citrix Bleed vulnerability and exploitation. See the kill chain, how Remote Code Execution (RCE) attacks easily bypass EDR tools, and how the Virsec Security Platform's Zero Trust security compensating controls provide protection, even in unpatched environments.
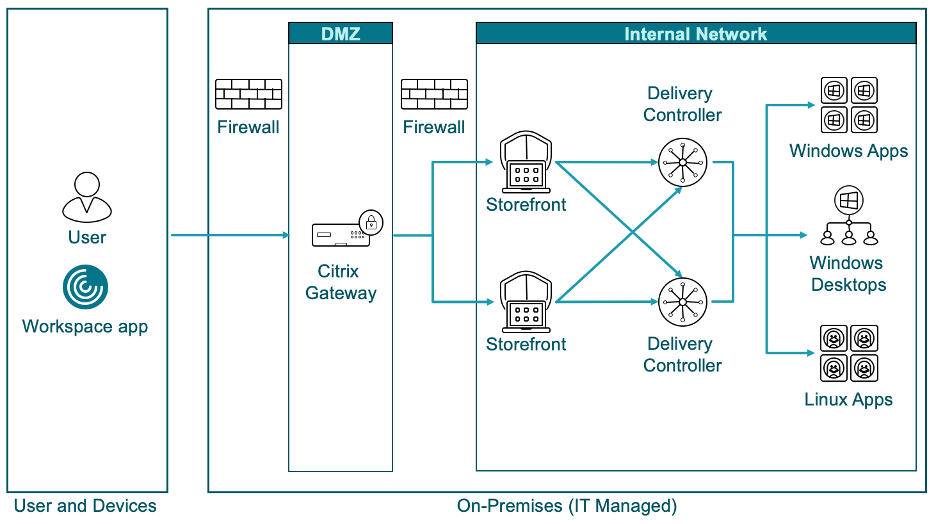
Citrix’s Netscaler Application Delivery Controller (ADC) and NetScaler Gateway enable enterprises to access their desktops and applications securely and remotely. Citrix also offers server applications, desktop virtualization, cloud computing, and networking products for Windows, Linux, and MAC platforms. Networking products converge and consolidate functionality such as Layer 4 Load Balancing, Layer 7 Traffic Management, Server Offloading, Application Acceleration, and Secure Remote Access, enhanced security policies, web–filtering policies for Internet users, user behavior analytics capabilities, to name a few. A block diagram showing how the Gateway works is as follows:
Citrix’s products serve over 100 million end-users, 400,000 customers, and 10000 partners in 100 countries.
Vulnerability
On October 10th, 2023, the NVD announced a vulnerability in Citrix’s ADC and Gateway, CVE-2023-4966, with a CVSS score of 7.5 High when configured as a Gateway (VPN Virtual Server, ICA Proxy, CVPN, RDP Proxy) or AAA Virtual Server. Due to the similarity in the underlying weakness with the Heart Bleed vulnerability in the Open SSL stack, this vulnerability was dubbed Citrix Bleed.
This vulnerability is present in:
- NetScaler ADC and NetScaler Gateway 14.1-8.50 and later releases
- NetScaler ADC and NetScaler Gateway 13.1-49.15 and later releases of 13.1
- NetScaler ADC and NetScaler Gateway 13.0-92.19 and later releases of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.164 and later releases of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.300 and later releases of 12.1-FIPS
- NetScaler ADC 12.1-NDcPP 12.1-55.300 and later releases of 12.1-NDcPP
CISA Known Exploited Vulnerability (KEV)
On October 18th, 2023, CISA released guidance indicating Threat Actors were actively exploiting a critical Remote Code Execution (RCE) vulnerability, CVE-2023-4966. Interestingly, Citrix itself classified this vulnerability with a score of 9.4 Critical.
Exploiting this vulnerability could disclose sensitive information, including session authentication token information that may allow a threat actor to “hijack” a user’s session.
Threat Analysis of Attack on Citrix ADC Appliance
When a Threat Actor pushes a very large buffer into the “Host” field of the HTTP Request, a vulnerable version of the Citrix gateway pushes a large amount of unexpected data, including the last authenticated user’s session token, into the HTTP Response.
The Threat Actor can then embed this session token in the following HTTP Requests and perform any action (such as extract valuable business and launch a ransomware attack) that the last authenticated user could perform without ever coming into possession of the said user’s password and without being impeded by MFA. By executing this attack repeatedly, the Threat Actor can extract the session cookies of other logged-in users can also be found.
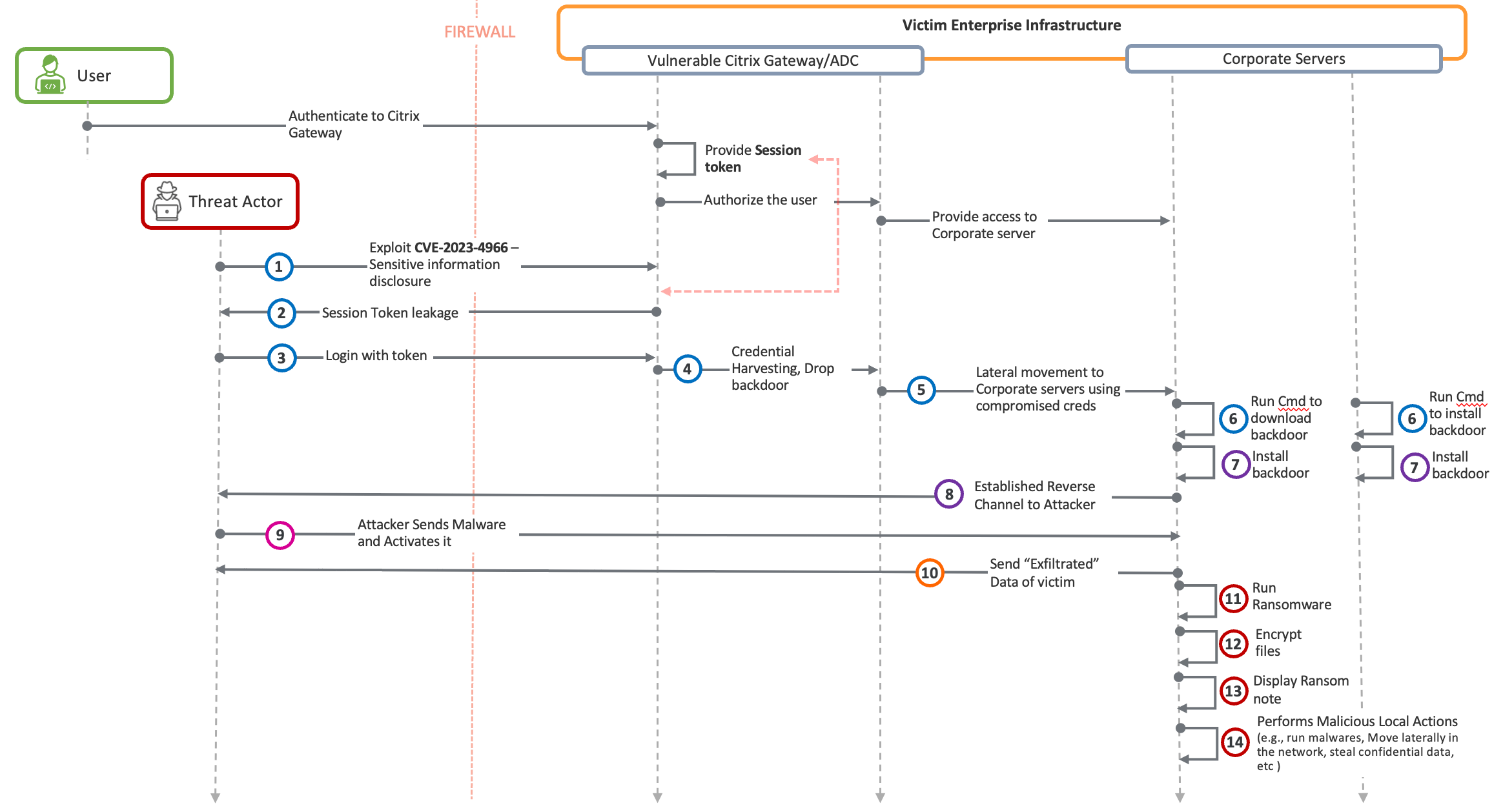
The Citrix ADC Exploitation Kill Chain
Below, we show the kill chain associated with this attack, as reported by Mandiant and AssetNote, who reverse-engineered Citrix code and analyzed the vulnerability almost identically. The color-coded legend at the bottom depicts the various attack stages.
- After the successful execution of Step 1, the Threat Actor comes into possession of the session token of the last logged-in user in Step 2.
- At Step 3, the Threat Actor starts communicating with the Citrix Gateway.
- In Step 4, the Threat Actor has acquired enough ability to perform various malicious actions such as credential harvesting, dropping web shells, etc.
- In Step 5, the Threat Actor performs lateral movement to as many downstream corporate servers as available.
- Once on the corporate servers, at Step 6, the Threat Actor proceeds to download a backdoor.
- At Step 7, the Threat Actor installs the backdoor.
- At Step 8, the Threat Actor has a fully functional reverse channel.
- At Step 9, this reverse channel allows the Threat Actor to download more malware onto the corporate server.
- At Step 10, the malware facilitates the dispatching of high-value confidential information stored on the said corporate server.
- Once the Threat Actor has compromised confidential information, they are ready for the next attack stage, which involves encrypting files at Steps 11 and 12.
- Once the ransomware has finished executing, the malware of Step 11 displays a ransom note before pivoting to another victim and repeating steps 11 through 14.
What happens after an ISV announces a vulnerability, especially an RCE vulnerability?
The sad reality- nothing! Fortunately for those enterprises that have deployed Zero Trust Runtime Defense security controls like the Virsec Security Platform (VSP), an RCE vulnerability does not automatically translate into a breach. This acts as a compensating control that can keep the enterprise safe, even when it hasn’t patched one or more RCE vulnerabilities.
A Better Solution
Conventional EDRs are security controls that follow the default-allow-block-on-threat philosophy. The typical EDR implicitly relies on many assumptions that Threat Actors circumvent routinely. One example of such abuse is the unhooking of the telemetry hooks that the EDR relies on. Unfortunately, the skills of Threat Actors often exceed the skills of both the practitioner and the AI/ML algorithm combined. It's no wonder cyberattacks continue to blindside EDRs. An EDR that unknowingly lets malicious code execute, even for a millisecond, is of questionable value. Those precious milliseconds are enough to unload, stop, or corrupt the EDR. At that point, the EDR is asleep at the wheel.
By contrast, true Zero Trust Runtime Defense security controls built with the default-deny-allow-on-trust (aka Positive Security) philosophy restrict the workload from processing code, threads, and child processes influenced by the Threat Actor. Positive Security Control protects the workload by allowing only such code, threads, and child processes that the enterprise explicitly trusts. This default-deny-allow-on-trust approach of the Positive Security Model ensures that no malware, no matter how sophisticated, can execute even one instruction on a victim workload, even if the Threat Actor has infiltrated that workload using stolen administrative credentials.
With that in mind, let’s reexamine the kill chain of the Citrix Bleed attack in the context of Virsec’s VSP:
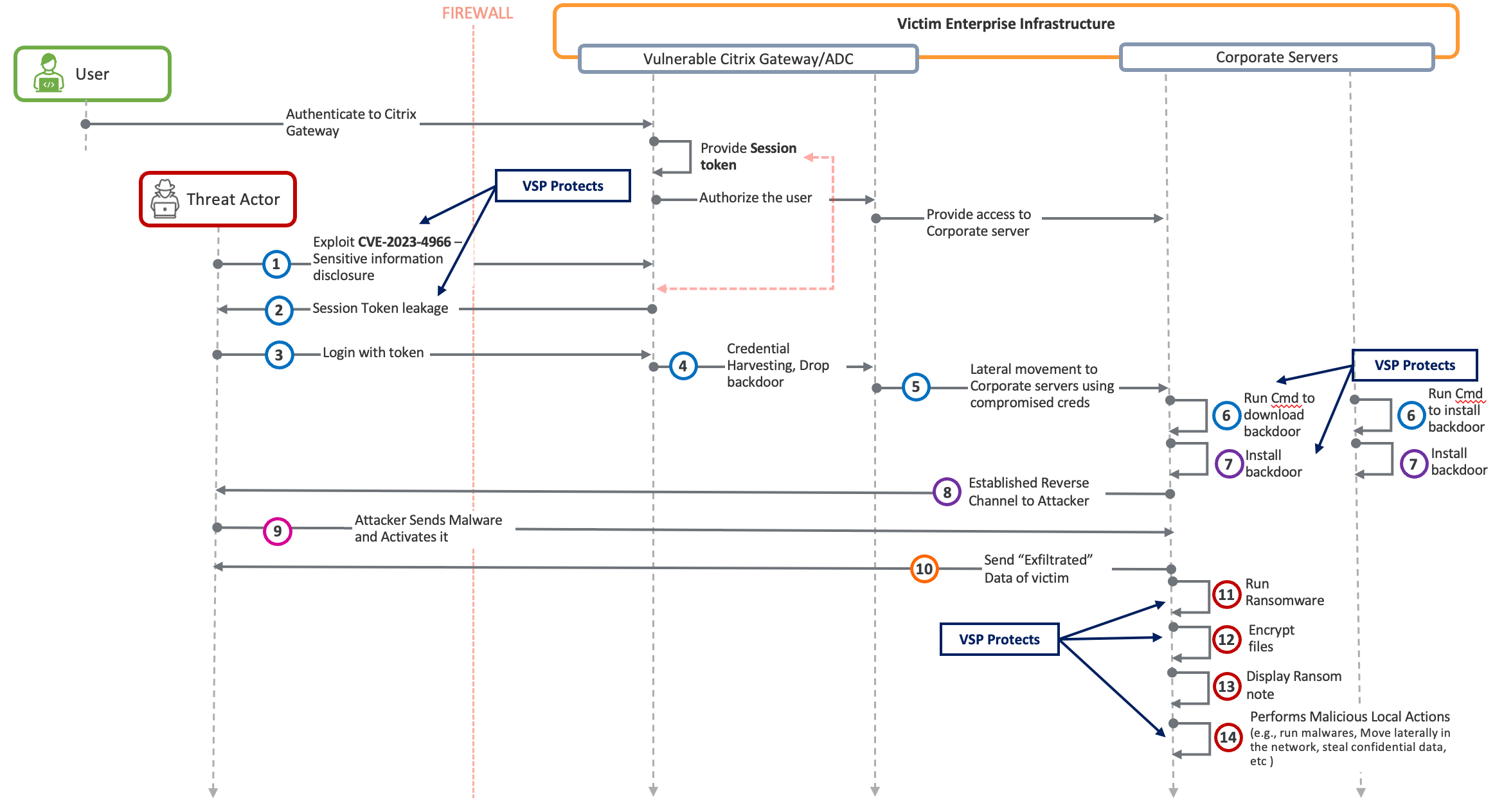
Virsec’s VSP can protect Citrix ADC and Gateway deployments against cyberattacks at Step 3 without needing any Threat Feeds, YARA rules, Behavioral, or Heuristic Signatures.
Conclusion
In today's fast-paced business environment, it can be a constant challenge for even the most mature organizations to keep their enterprise software updated. With the daily influx of patches, it can feel like a never-ending task. Unfortunately, this also means that Threat Actors are always ready to exploit any vulnerabilities that might arise, especially when it comes to Remote Code Execution (RCE) attributes.
By implementing a Zero Trust Runtime Defense solution like the Virsec Security Platform, enterprises can attain a level of cyber hygiene that surpasses the capabilities of traditional EDR technology. This is crucial because sophisticated malware has the ability to disable, unload, or terminate EDR processes and effectively evade detection. With the deployment of a robust Zero Trust solution, organizations can fortify their workloads against such threats and ensure comprehensive protection.
To learn more about Virsec VSP, please visit us at www.virsec.com
For more detailed information on Zero Trust Runtime Defense and how we protect vulnerable legacy workloads, visit www.virsec.com.
Don't miss our security insights, and subscribe to our blog now.