This blog post discusses CVE-2023-4911, a high-severity buffer overflow vulnerability in the GNU C library's dynamic loader library that allows a threat actor to gain root privileges on a vulnerable victim workload. We also explain how sophisticated attackers use Living off the Land Binaries (LOLBin) malware and walk through the vulnerability kill chain. The Virsec Security Platform (VSP) protects against these attacks by identifying and preventing any code executed by the attacker, safeguarding the victim's workload by taking protective measures like terminating the user's session, quarantining malicious executables, or closing the network socket used for communication with the attacker's control center.
Background: On October 3rd, 2023, the US-CERT’s National Vulnerability Database (NVD) identified a high-severity buffer overflow vulnerability, CVE-2023-4911 (CVSS Score 7.8; High), in the GNU C library’s dynamic loader library, called ld.so. This library finds and loads shared libraries needed by an executable. This vulnerability allows a Threat Actor to gain root privileges on a vulnerable victim workload. This vulnerability has been present since April 2021 in glibc version 2.34 to present (version 2.38). Millions of Linux workloads worldwide use the aforementioned dynamic loader library.
Exploitation Risk: This vulnerability can allow a Threat Actor who has previously infiltrated the enterprise to gain root privileges on the victim workload. Armed with elevated privileges, the victim workload’s user space and kernel are entirely under the control of the Threat Actor, who can then perform any arbitrary action. Depending on the attacker’s objectives, the Threat Actor can propagate within the network and initiate various attacks, including data exfiltration, credential theft, ransomware, denial of service, crypto mining, and execute botnet activities.
In-Depth Analysis: Linux executables with the SetUID, SetGUID Access flag set, and others with defined “capabilities” read the GLIBC TUNABLES environment variables to tune the executable’s behavior. Unfortunately, due to buffer overflow vulnerability in the parse_tunables function in ld.so. An attacker can overrun the GLIBC_TUNABLES environment variables and gain complete administrative control over the vulnerable workload. Per RedHat (Version 2.23, this vulnerability is exploitable by any local user and can lead to privilege escalation when combined with almost any SUID-root binaries. One saving grace, at least thus far, is that the Threat Actor doesn’t know the exact location or size of the buffer involved in this vulnerability, which means they must resort to brute-force means of exploitation. This position may change since the glibc authors have published more significant details.
Advanced Threat Techniques: Having gained elevated privileges, sophisticated attackers can use LOLBin (Living off the Land Binaries) malware instead of easily detectable executable malware. LOLBin malware leverages OS runtime utilities like bash and awk to execute commands, manipulate permissions, gather process information, extract credentials, access SSH private keys and known_hosts files, encode and encrypt data, inspect bash history, and even remove itself.
Kill Chain: We can divide the attacker’s activities into five stages: reconnaissance, persistence, weaponization, exploitation, and exfiltration.
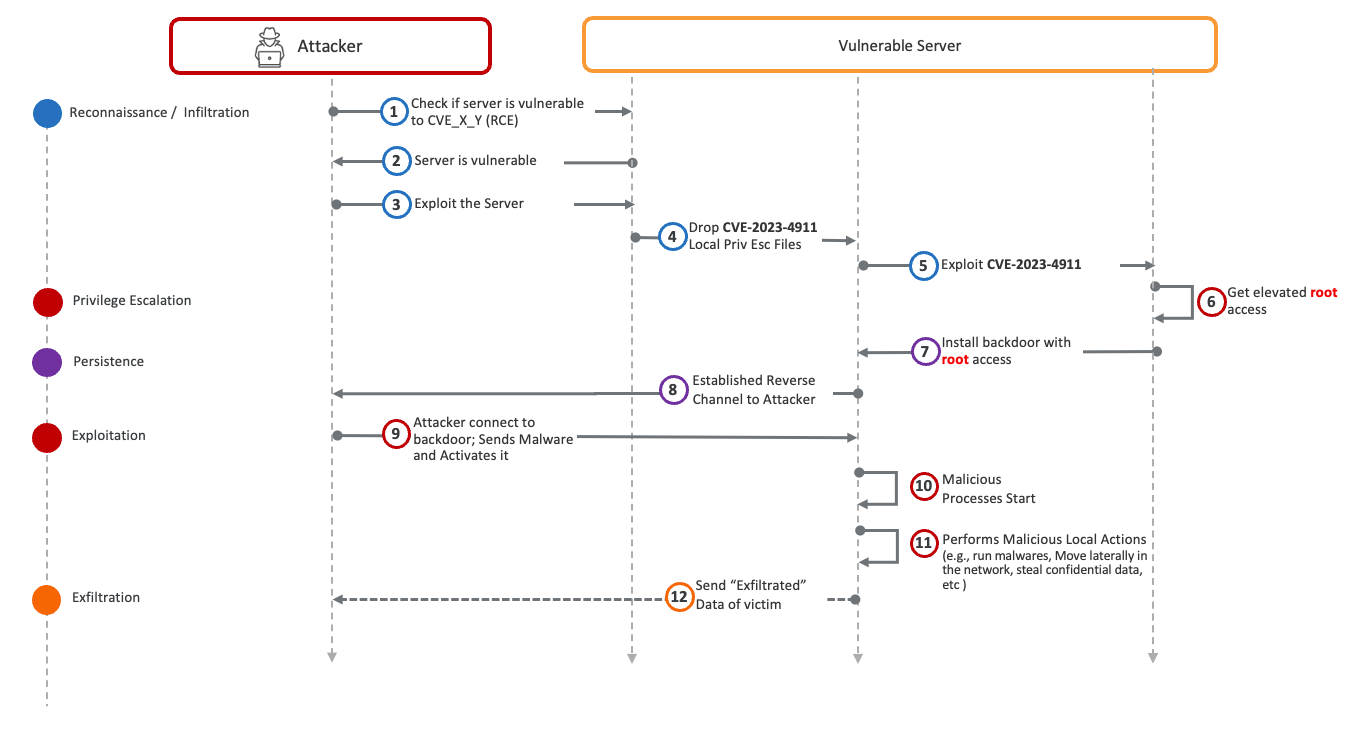
During the reconnaissance stage, Threat Actors leverage tools like Shodan to locate potentially vulnerable servers. Once found, the attacker verifies if the target uses the vulnerable glibc library. Subsequently, in the persistence stage, the attacker establishes a reverse channel for control. In the weaponization stage, the attacker deploys the appropriate malware (such as LOLBin scripts) for further reconnaissance, lateral movement, and data exfiltration. In exploitation, the attacker performs malicious actions like lateral movement and data theft. Finally, in the exfiltration stage, critical data is sent back to the Threat Actor’s command and control center.
Virsec Security Platform (VSP) Protects: VSP plays a crucial role in this scenario. It identifies, within milliseconds, any code executed by the attacker during the reconnaissance stage as being influenced by the attacker.
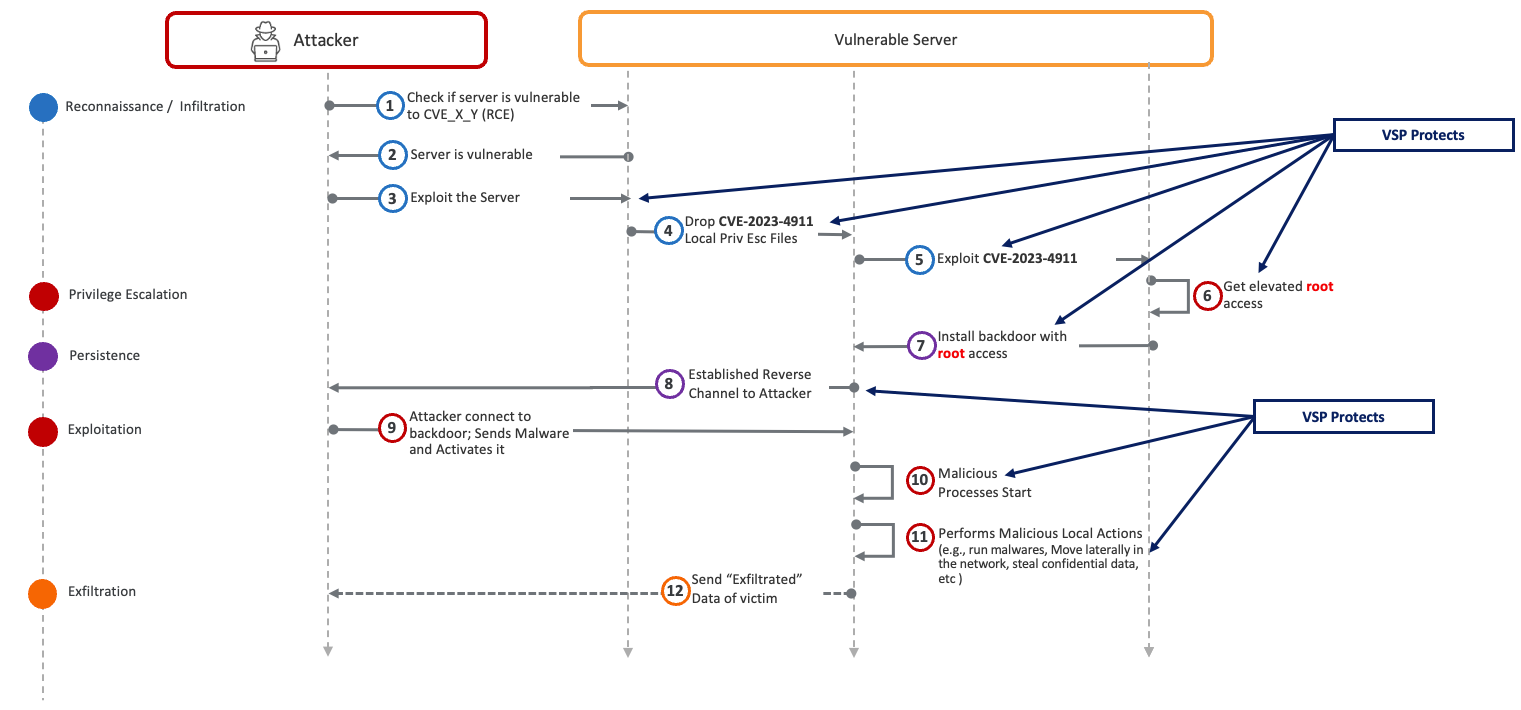
Before a Threat Actor can exploit the RCE vulnerability at Step 3, VSP’s ACP Engine recognizes that the targeted legitimate application is not authorized to obtain a shell. As explained earlier, since the vulnerability CVE-2023-4911 involves local privilege escalation, the Threat Actor must leverage some local malware that will generate large buffers to overrun the GLIBC_TUNABLES environment variable at Step 4.
Virsec’s HMM Engine prevents such malware from executing even one instruction. Virsec’s ACP Engine also stops steps 5, 7, and 11, whereas Virsec’s HMM Engine will stop Step 10 in the kill chain. VSP safeguards the victim's workload by taking protective measures, such as terminating the user’s session, quarantining the malicious executables, or closing the network socket used for communication with the attacker’s control center. As a result, the Threat Actor's attempts are unsuccessful.
Demonstration: Watch a video showing how the Virsec Security Platform (VSP) thwarted Threat Actors that targeted these vulnerabilities at https://youtu.be/USj4_3-4B2c
Key Takeaways:
- Enterprises must respond promptly when information on Remote and Local Code Execution vulnerabilities in deployed software becomes known. Threat actors are a constant threat, and the question isn’t if they will attack but when.
- This vulnerability has been present in the GNU glibc code base since April 2021; it is challenging to determine if Threat Actors have been using it since then or if they started using it in October 2023 for the first time.
- The Virsec Security Platform (VSP) is a proactive compensating control, offering protection even when the enterprise cannot apply software patches promptly. CISOs can rest assured that VSP will safeguard their systems.
For more information about the Virsec Security Platform (VSP) and how we protect vulnerable legacy workloads, visit www.virsec.com.
Don't miss our security insights, and subscribe to our blog now.





