See how it works..
before:
10,000 CVEs
after:
1,000 CVEs
before:
20%
exploitable vulnerabilities
exploitable vulnerabilities
after:
0%
exploitable vulnerabilities
exploitable vulnerabilities
before:
RCE 3,000
after:
RCE vulnerabilities reduced by 100%
BEFORE:
KEVs 30%
AFTER:
0% KEVs
Introducing OTTOGUARD.AI by Virsec
Stop endless patching–autonomously guard your assets.
OTTOGUARD.AI transforms cybersecurity by eliminating the need for constant patch management.
Unlike traditional vulnerability remediation, OTTOGUARD.AI uses patented zero trust technology to instantly neutralize both known and zero-day threats at runtime—without patching. This shift to patchless protection delivers true zero Mean Time to Remediate (MTTR), autonomously stopping threats the moment they emerge.
With comprehensive workload vulnerability insights and autonomous application control, OTTOGUARD.AI instantly locks down your software supply chain at runtime, neutralizing threats in milliseconds.
We Reduce Your MTTR by 90%—Because Remediation Speed Matters
Lock down vulnerabilities in real time without patching
Mitigate
Mitigate 90% of Critical Vulnerabilities Without Patching
We block the exploit of vulnerabilities autonomously and with zero-time-to-patch.
Prevent
Prevent Ransomware in Milliseconds
Stop ransomware, malware and zero-day attacks at the root. Zero dwell time, zero downtime.
Protect
Protect Your Software Supply Chain from Source to Runtime Autonomously
Know exactly what’s deployed, ensure it’s safe, and maintain integrity at every step—with autonomous application control.
Autonomously Mitigate Known and Unknown Vulnerabilities
in Real Time
The Reality
without OTTOGUARD.AI by VIRSEC
- Drowning in dashboards and endless alerts
- Constant fire drills and emergency patches
- SLA breaches due to unpatched critical vulnerabilities
- Ransomware, bad code, and legacy software risks piling up
A DAY
with OTTOGUARD.AI by VIRSEC
- Checking what’s been mitigated—not what’s at risk
- No more board meetings explaining why things keep getting worse
- Endless patching cycles and downtime risks neutralized
- No false positives, no alert fatigue
- Risk exposure brought to zero
30 days
with OTTOGUARD.AI by VIRSEC
- Zero Mean Time to Remediate (MTTR)–emergency patching eliminated.
- Complete software supply chain visibility. Know if your software is safe and trusted.
- Mitigation without patching–vulnerabilities mitigated before they are exploited.
- Reduced risk exposure with zero touch automation for your security and application teams.
Mitigate Vulnerabilities
in Your Legacy Software—Without Patching
Autonomously protect end-of-life and unpatchable software from evolving threats—without patching.
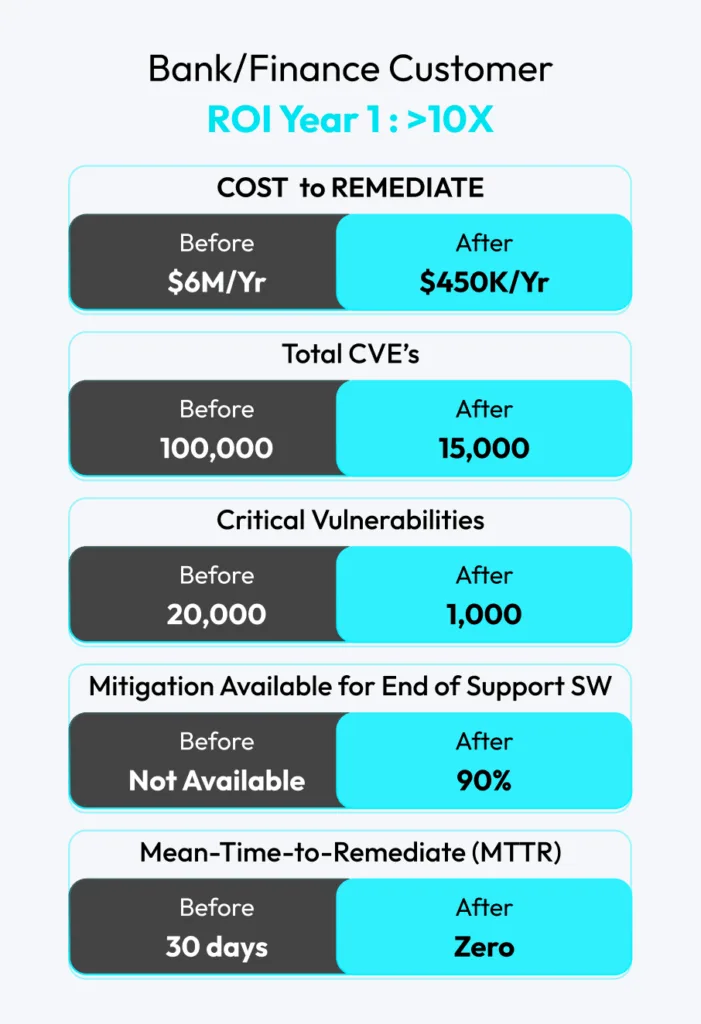

10x your security ROI.
Transition from patching chaos to autonomous runtime protection in no time.
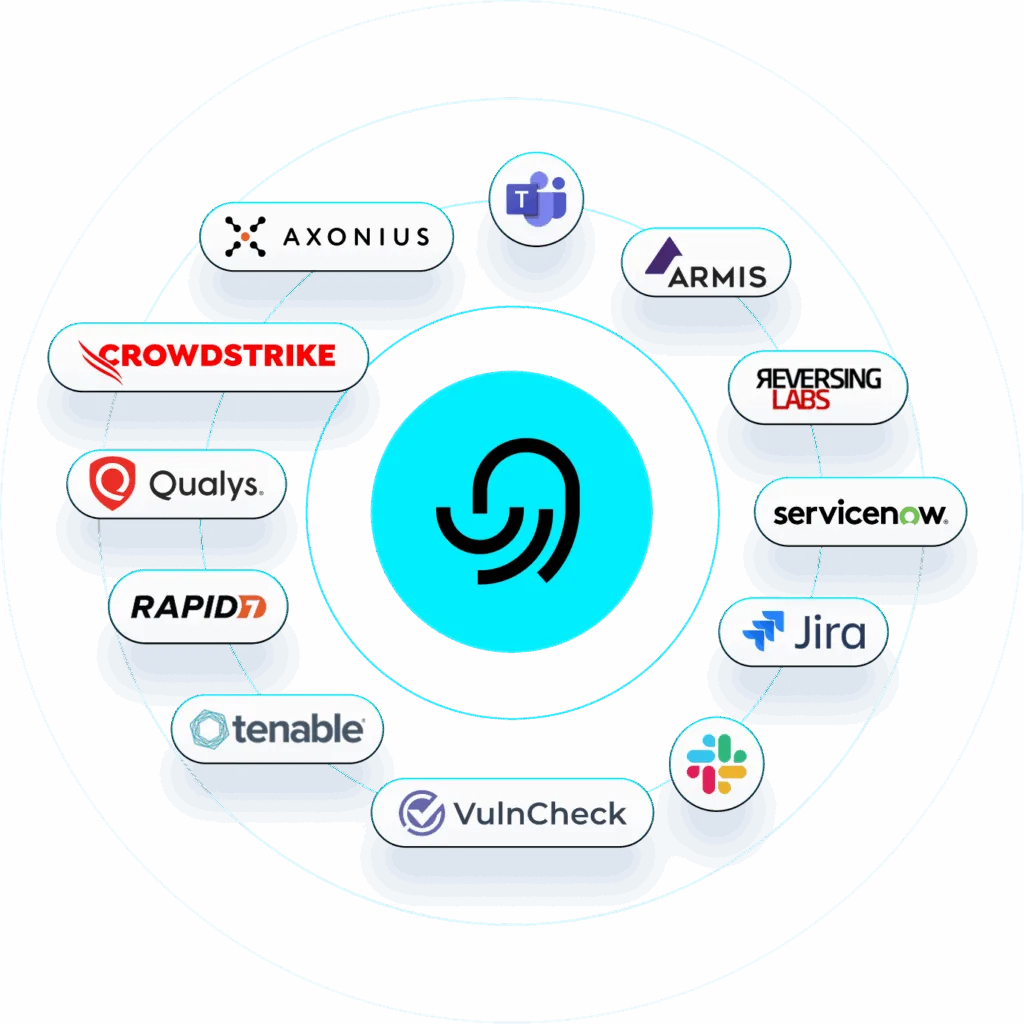
Better Together Ottoguard.ai integrates right into your stack
Ottoguard.AI plugs in via API and automation to your existing incident response, asset management, vulnerability, and ticketing tools
Secure What Matters—Mitigate Exposure Now.
Take Control. Don’t Just Manage. Mitigate.