Learn about the CVE-2023-33246 vulnerability in Apache RocketMQ, which allows unauthenticated users to execute Remote Code Execution attacks. We'll highlight the five stages of the threat actor's activities and how proactive compensating controls can help protect applications and workloads against these attacks.
Background: CISA maintains the Known Exploited Vulnerability (KEV) catalog, an authoritative source of vulnerabilities exploited in the wild. On September 6th, 2023, CISA announced adding a new vulnerability, CVE-2023-33246, in the open-source Java-based Apache RocketMQ application into its KEV catalog.
Apache RocketMQ is a popular high throughput, high reliability, low latency messaging, eventing, and streaming data processing middleware platform open-sourced by China’s Alibaba in 2012. It actively competes with ZeroMQ, RabbitMQ, ActiveMQ, and Kafka.
CISA reports that Threat Actors have abused this vulnerability in Apache RocketMQ since June 2023. Based on the exploit code variances, it is evident that at least five cybercriminal gangs are actively abusing the vulnerability. Several gangs are using the vulnerability to run the Monero Cryptocurrency Miner. The abuse has reached the point that CISA advises users to upgrade to version 5.1.1 or quit using this product.
Deeper Dive into the Attack: On May 23rd, 2023, the Apache RocketMQ team notified its users about a Remote Code Execution (RCE) vulnerability in all versions through 5.1.0. This notification shows two ways to abuse the Apache RocketMQ vulnerability. One method involves using the update configuration function to execute commands as the system users that RocketMQ is running as. The second method involves forging the RocketMQ protocol content.
This vulnerability is especially potent because even an unauthenticated user can gain system-level privileges and mount an RCE attack on the victim. Three Apache RocketMQ services, the NameServer, Broker, and Controller service, were never meant to be exposed to the Internet.
The Threat-Actors have cleverly avoided detection by abusing LOLBINs or malware that does not use specially constructed malware. Instead, it uses OS runtime utilities such as bash, awk, etc., for running commands to modify permissions, enumerating processes, dumping credentials, reading the SSH private keys and the “known_hosts” file, encoding and encrypting data, reading the bash history, and even deleting itself.
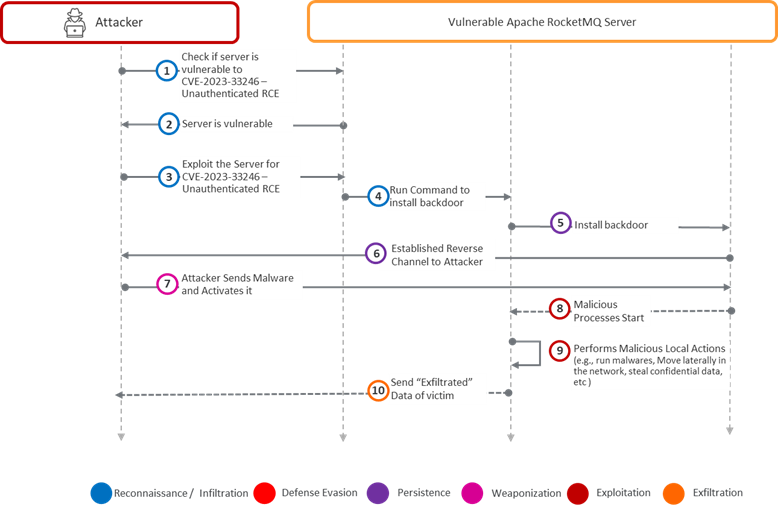
Kill Chain: The following five stages describe the Threat Actor’s (TA) activities. In the reconnaissance stage (Steps 1 through 4 below), the TA leverages tools such as Shodan to hunt down workloads that could be hosting Apache Rocket MQ> On finding a potentially vulnerable server, the TA tests if the server is using Apache RocketMQ version 5.1.0 or below. In the persistence stage (Steps 5 and 6 below), the TA establishes a reverse channel from the victim workload to the TA’s Command Control center. In the weaponization stage (Step 7 below), the TA deposits the appropriate malware (such as the Monero Miner, scripts for lateral movement, etc.). In the Exploitation stage (Steps 8 and 9 below), the TA performs all the required malicious actions, such as lateral movement, stealing confidential data that the TA can monetize on the dark web, etc. Finally, in the exfiltration stage (Step 10), the TA returns critical data to its command control center.
In many cases, the TA was content with running the Monero Crypto Miner for long periods for financial gain. In other cases, critical information from the victim was put into several paste bins for sale to bidders.
How does Virsec Help? Please see the updated kill chain below. Virsec’s VSP Controls recognize in milliseconds that the first piece of code that the TA executes on the victim workload as part of the reconnaissance stage (step 4) is attacker-influenced code. Even before the action in Step 4 executes, VSP’s Application Control Engine recognizes that no legitimate application on the workload is authorized to execute such an action.
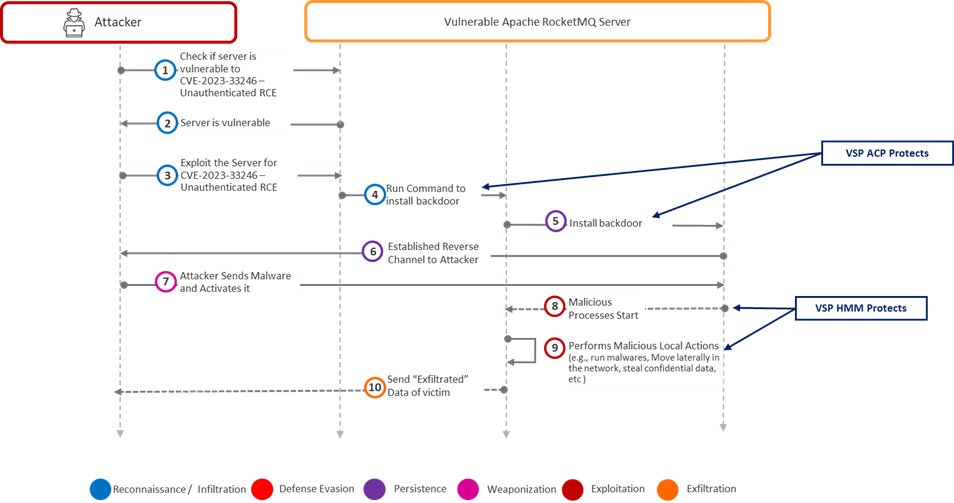
VSP, therefore, protects the victim server by executing a protection action such as restarting the Apache RocketMQ server or terminating the network socket on which the TA communicates with their Command Control Center.
Demonstration:
Watch how VSP stops the Apache Rocket MQ attack in this video: https://youtu.be/mzTsfHu2YHc.
Summary:
- Organizations must take urgent action when they become aware of a Remote Code Execution vulnerability in deployed code. Threat Actors are lurking in the shadows, and it is not a question of whether the TA will come but when they will descend.
- Threat Actors have been abusing this vulnerability since June 2023. Here we are four months later, still experiencing the shock waves. Many CISOs have been unable to or were caught unaware that a patch existed and they could have deployed.
- The Virsec Security Platform (VSP) is a proactive compensating control that can protect enterprises even if they do not apply software patches for whatever reason. The CISO can sleep better knowing that VSP will protect their workloads.
Read more information about the Virsec Security Platform (VSP) and how we protect vulnerable legacy workloads.
Don't miss our security insights, and subscribe to our blog now.