Join us as we do a deep threat analysis into the vulnerability and exploitation of Netwrix Auditor and discover ways to safeguard against RCE attacks. Gain valuable insights and protect your workloads from potential threats.
Netwrix's Auditor software is a popular Enterprise IT Audit Software that helps to detect security threats, prove compliance, and increase IT Team efficiency. According to Netwrix, over 13,000 organizations across 100 countries, including the US and Canada, rely on Netwrix. Some of Netwrix's customers include Airbus, Virgin, Allianz, UK's NHS. The vulnerability exists in all versions of Netwrix before version 10.5.
On July 11th, 2023, CISA released an alert indicating Threat Actors were actively exploiting a critical Remote Code Execution (RCE) vulnerability, CVE-2022-31199, with a CVSS score of 9.8, in Netwrix's Auditor software. Other reports indicate that the threat actor involved in exploitation is the Russian Threat Actor, code-named TA505.
What made matters worse was that since the Netwrix Auditor service operates with extensive privileges in an Active Directory environment, an attacker would gain elevated privileges, thereby compromising workloads in the entire domain.
Interestingly, even though the NVD first reported the vulnerability in July 2022, its customers failed to patch their installation of Netwrix Auditor. As bad as that sounds, this is the reality most enterprises live in. It isn't easy to keep up with patching since it can disrupt business continuity.
Threat Analysis of Attack on Netwrix Auditor
The root cause of the vulnerability was that the Netwrix Auditor deserialized untrusted data without establishing trust. Next, the malicious payload (TrueBot malware) lurking in the untrusted data would execute on the victim server.
CISA's cybersecurity advisory for this vulnerability indicates that after successful infiltration through the Netwrix Auditor vulnerability, the attackers used a variant of the TrueBot malware (also known as Silence Downloader) for the following stages of exploitation. TrueBot is a botnet used by Threat Actors like the CL0P Ransomware gang to collect and exfiltrate critical information from its victims using an open-source data exfiltration tool called Teleport which creates a reverse encrypted SSH channel on the workload. After TrueBot collected enough valuable information, the threat actor deployed CL0P Ransomware on the victim's workload. To learn more about how CL0P ransomware works, read our blog on the attack on Progress Software's MoveIT software.
Can the Remote Code Execution (RCE) vulnerability in Netwrix Auditor be Exploited otherwise?
As with any RCE vulnerability, the vulnerability simply opens the door to the victim. What the attacker does next is entirely up to the attacker. It is, therefore, naïve to think that there is only one Threat Actor, TA505, at work here and that only TrueBot/ CL0P ransomware is involved.
Why do we bring up this issue? We hear of many CISOs' taking reactive steps, such as updating their EDRs with TrueBot/ CL0P ransomware Indicators of Compromise. As a reality check, NVD reported the Netwrix Auditor vulnerability on July 11th, 2022, a year ago. It would be a huge mistake to think it is just the TA505 gang dipping its hands in the cookie jar.
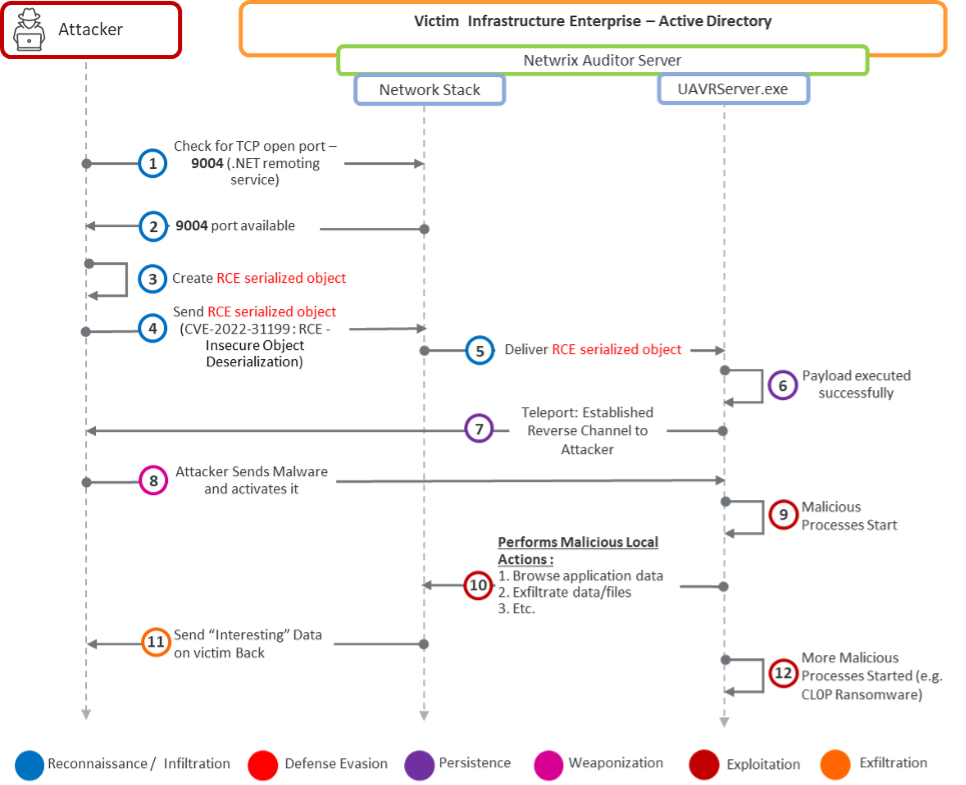
The Netwrix Auditor Exploitation Kill Chain
Shown below is the kill chain associated with the cyberattack launched by TA505. The color-coded legend at the bottom depicts the various attack stages.
After the successful execution of Steps 1 and 2, the Threat Actor has found a victim enterprise they can compromise. In Steps 3 to 6, the Threat Actor exploits the Deserialization of the Untrusted Data vulnerability (CVE-2022-31199) described above, and in Step 7, the backdoor gets instantiated. In Steps 8 and 9, the Threat Actor leverages and activates the Teleport software to drop TrueBot malware on the Netwrix and adjacent servers. In Steps 10 and 11, the Threat Actor extracts "valuable" data that they will need in the following stages of the attack. These two steps are a significant milestone in the Double Extortion stage of the overall attack. Many victims believe they need not pay the ransom because they can recover their workload from a recent backup. In such cases, the Threat Actor forces the hand of the victim by releasing some of the exfiltrated information. Hence the term double extortion!
The paths of various Threat Actors can diverge after Step 11. The TA505 Threat Actor chose to go down the path described in Step 12: execute the CL0P Ransomware on the victim workload(s).
What Do Most Enterprises Do When They Get CISA Alerts on Known Exploited Vulnerabilities?
On receiving CISA's alerts, many organizations with excellent cyber hygiene will immediately start patching the vulnerabilities. The harsh reality is that most enterprises fail to act. What else explains why a vulnerability reported on July 11th, 2022, is being reported as being actively exploited by CISA one year later? By not patching on time, the enterprise provides red meat to Threat Actors worldwide.
Fortunately, with recent advancements in cyber security technology, some alternatives can keep the enterprise safe, even when it hasn't patched vulnerabilities.
What Are These Alternatives?
Most conventional EDRs implicitly rely on many assumptions that attackers circumvent routinely. Some of the leading tenuous assumptions that EDRs leverage are (a) the telemetry hooks inserted by the EDR cannot be unloaded, stopped, or corrupted, and (b) Threat Actors leverage a finite set of TTPs. Unfortunately, the skills of Threat Actors often exceed the skills of both the defender and the AI/ ML algorithm combined. To make matters worse, Threat Actors have the first movers' advantage; no wonder why attacks continue to blindside EDRs.
By contrast, Security Controls built with the Default Deny (aka Positive Security) philosophy restrict the workload from processing Threat Actors influenced data, files, or processes. Positive Security Control protects the workload by allowing only such data, files, and processes that the enterprise explicitly trusts.
This Default-Deny-Unless-Explictly-Trusted approach of the Positive Security Model ensures that no malware, no matter how sophisticated, can execute even one instruction on a victim workload even if the Threat Actor has infiltrated that workload using stolen administrative credentials.
Therefore, Positive Security Control stops the attack even if the workload lurks unpatched or unknown vulnerabilities. Even more importantly, Positive Security Control protects the workload BEFORE it experiences damage.
By contrast, the EDR follows the Default-Allow-Implicitly-Trusted approach. An EDR that unknowingly lets malicious code execute, even for a millisecond, is of questionable value. Those precious milliseconds are enough to unload, stop, or corrupt the EDR. At that point, the EDR is asleep at the wheel.
With that in mind, let's reexamine the kill chain of the Netwrix Auditor's attack in the context of Virsec's VSP, a Positive Security Control.
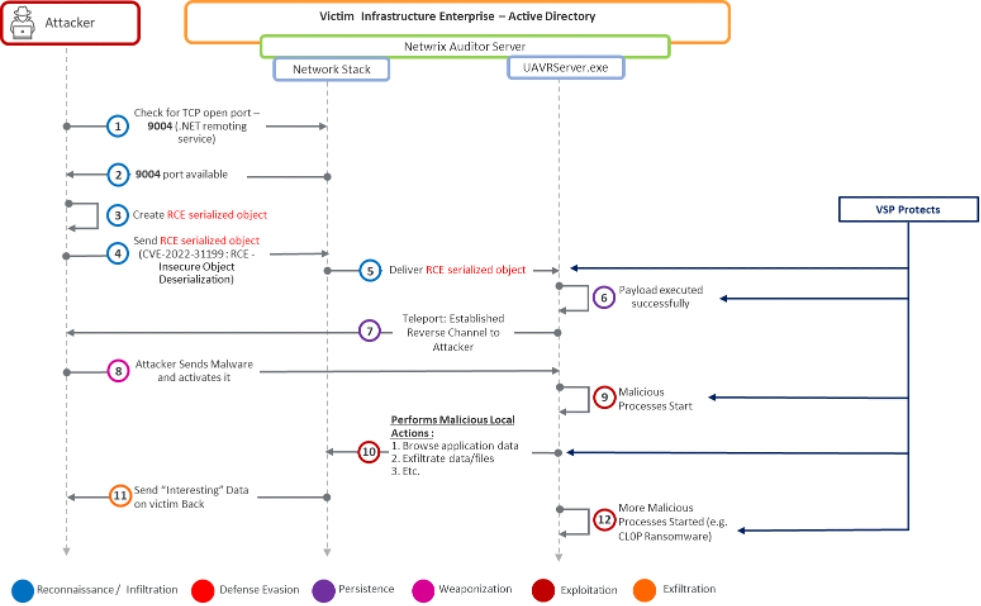
Virsec's VSP can protect Netwrix Auditor server deployments against cyberattacks at Step 5 without needing any Threat Feeds, YARA rules, Behavioral, or Heuristic Signatures.
Summary
Even with the best intentions, keeping enterprise software updated is challenging, given the daily volume of patches. Unfortunately, threat actors are never far when patches are not applied, especially if one or more unpatched or unknown vulnerabilities have Remote Code Execution (RCE) attributes. Almost all alerts in CISA's catalog of Known Exploited Vulnerabilities have RCE attributes.
Sophisticated malware can disable, unload or terminate EDR processes and suppress telemetry. By deploying VSP, a Positive Security Control, on their workloads, enterprises can achieve cyber hygiene that is impossible with EDR technology. Learn more about Virsec's Positive Security Model in this blog.
To learn more about the Virsec Security Platform (VSP), please visit us at www.virsec.com
Don't miss our security insights, and subscribe to our blog now.