Microsoft ended Windows Server 2012 support on 10/10/23. We'll explore several options for organizations running critical workloads and applications on these legacy servers to protect them from threat actors waiting to exploit unpatched vulnerabilities.
In addition to the challenge of dealing with a reduced budget, CISOs are now faced with the end of Microsoft's support for Windows Server 2012. This leaves many with their backs against the wall, forced to make some tough decisions:
- Option 1: Signing a contract with Microsoft for the very pricey Extended Security Updates (ESUs) service for the Windows 2012 servers in the infrastructure. Spending $4,000 to protect a single 12-year-old server feels wrong.
- Option 2: Moving on-prem Windows 2012 servers into the Azure Cloud to avoid paying top $$ for ESUs. This migration is easier said than done. Most of the developers are long gone. What happens if the setup and configuration go south? No CISO wants to play that deal.
- Option 3: Risk upgrading (potentially revenue-generating) apps to a newer OS. The developers knew about this deadline many years ago, but here we are!
- Option 4: Staking the enterprise's security strategy on Microsoft's guidance and hoping to fly on a "wing and a prayer." Keeping ahead of threat actors is hard enough when patches are coming. Now, with no patches coming ever, how is the CISO supposed to keep their sanity intact?
What is worse than patching periodically? That would be no patch coming ever again! We all know that patching is a nuisance that results in frantic activity, loss of revenue, reputation, and many other undesirable outcomes at the very minimum. But then not patching fast enough is an even worse alternative. It serves as an open invitation to threat actors. The end-of support looming and the patching option fading away right before their eyes cannot be a good feeling for the CISO.
Why are threat actors waiting for this day to arrive? Threat actors know that those CISOs who haven't taken the pricey option or migrated their Windows 2012 servers to Azure Cloud will have only some "guidance" from Microsoft if a vulnerability surfaces. Usually, this guidance involves tedious work to implement.
Take the case of the critical vulnerability CVE-2013-3900. A Win 2003 and Win 2008 server (both out-of-support servers) suffering from this vulnerability will not validate the signature of a Windows executable properly and mistakenly allow signed but vulnerable code and drivers to execute, thereby allowing threat actors to execute malicious and arbitrary code of their choosing. In this case, Microsoft's "guidance" involves making tedious changes to every vulnerable Win 2003 and Win 2008 server. Imagine putting in this much work for 1000s' of such servers in the infrastructure. In this case, there is some guidance available. There are some cases where there is no mitigating guidance available.
Many organizations will either not implement the guidance or take their time doing so. This behavior pattern gives threat actors plenty of time to take advantage without being rushed. There is no race against time involved!
What can enterprises do to reduce end-of-support risks? Intel's visionary founder and ex-CEO Andy Grove famously said, "Only the Paranoid Survive." A forward-leaning CISO can use Andy Grove's advice on a "strategic inflection point" to deploy a compensating control that insulates their workloads against remote code execution and privilege escalation vulnerabilities even if the workload can't be patched. Such a compensating control leverages the Default-Deny-Allow-On-Trust (aka Positive Security) principle, which means that:
- No malware (past, present, or future) will execute, and
- Even if vulnerable, all authorized infrastructure and application layer code will not allow attacker-influenced code to derail the legitimate code from its guardrails.
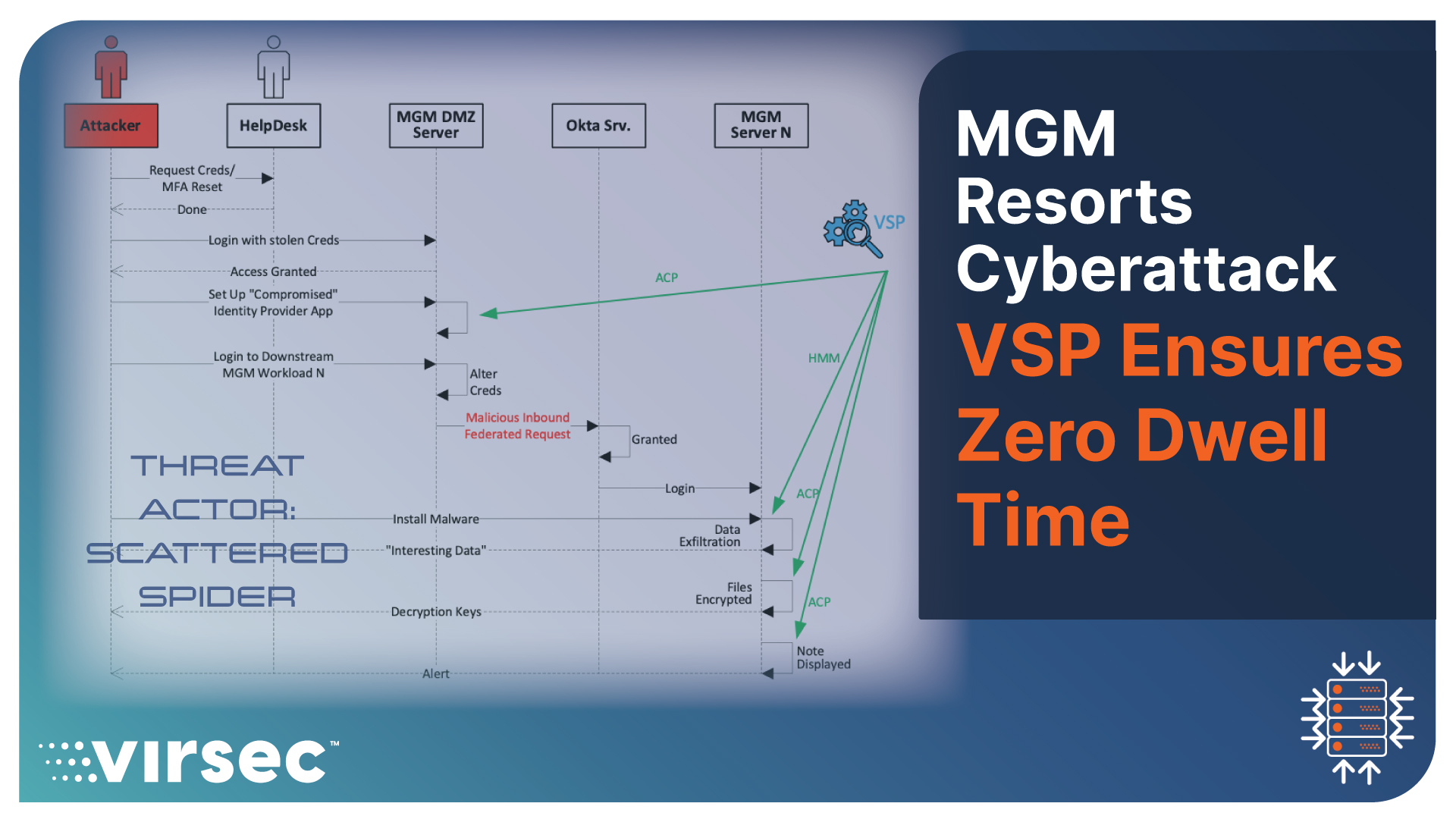
Why is Positive Security Control demonstrably more effective than EDRs? Unlike the positive security control's Default-Deny-Allow-On-Trust approach, the EDR takes the opposite Default-Allow-Block-On-Threat approach. All that a threat actor must do is implement a novel form of threat to get past the EDR's defender. With adversarial AI gaining momentum, conjuring uncatalogued threats is as easy as 1-2-3. Don't let the EDR vendors have you believe that they've got every threat actor's number. That would take mind-reading superpowers that EDRs (and frankly, no one) do not have. The graphic below shows how much of an efficacy gap between Virsec's VSP (a Positive Security Model) and the leading EDR when tested against Safe Breach, a leading cyber-attack simulator platform.
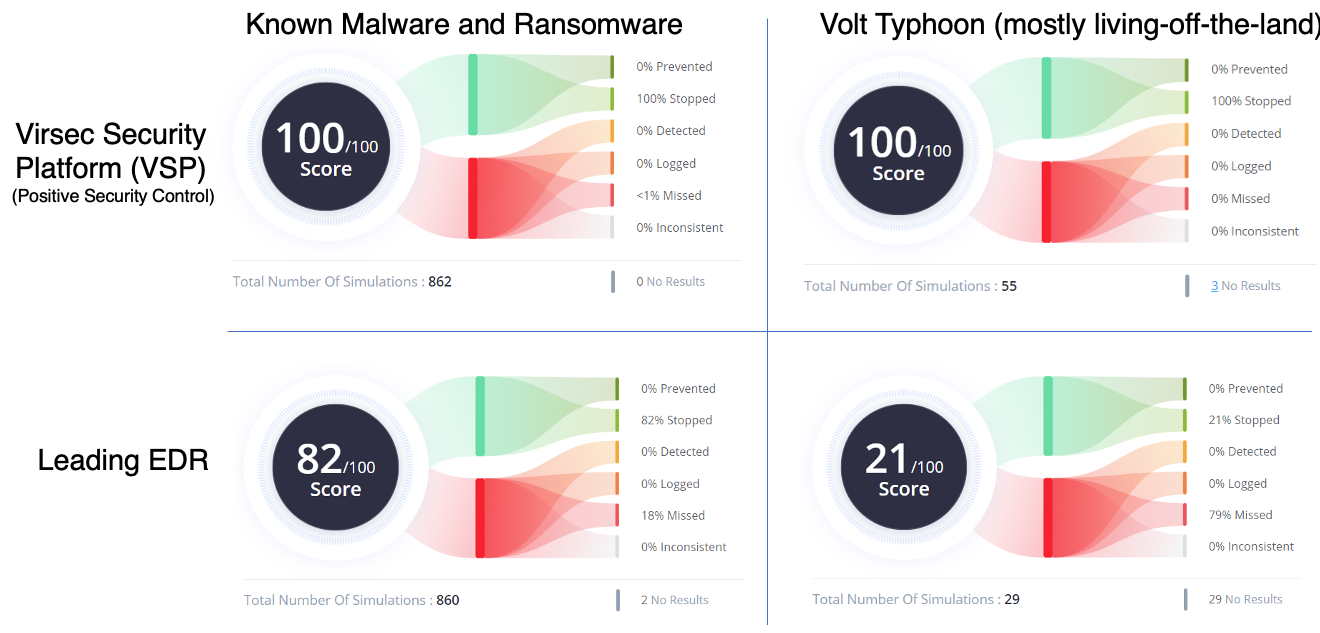
What is even more glaring is that the difference in efficacy diverges even more when the attacker uses Living-Of-The-Land (aka fileless) malware. Such malware brings EDRs to their knees, whereas the Positive Security Model control continues to perform at top efficacy.
Summary
For those still running legacy Windows Server 2012 and who need to ensure security for their workloads and applications, there is a 5th option available. Virsec's Positive Model Security Controls, also known as Default-Deny-Allow-On-Trust, provide unmatched effectiveness and peace of mind, even in cases where the workload and applications remain unpatched. Learn more about Virsec's Positive Security Model in this blog.
For more information about the Virsec Security Platform (VSP) and how we protect vulnerable legacy workloads, visit www.virsec.com.
Don't miss our security insights, and subscribe to our blog now.