Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
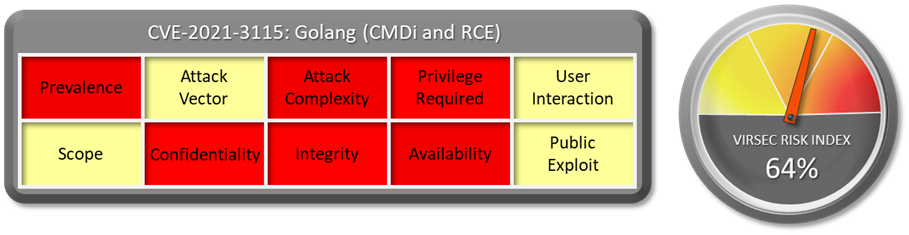
1.1 Vulnerability Summary
Go before 1.14.14 and 1.15.x before 1.15.7 on Windows is vulnerable to Command Injection and remote code execution when using the "go get" command to fetch modules that make use of cgo (for example, cgo can execute a gcc program from an untrusted download).
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
The CVSS Base score of this vulnerability is not provided in NVD.
1.3 Affected Version
Go before 1.14.14 and 1.15.x before 1.15.7 on Windows
1.4 Vulnerability Attribution
This vulnerability is disclosed by MITRE.
1.5 Risk Impact
The language is often referred to as Golang because of its domain name, golang.org, but the proper name is Go. Go Lang is very popular interpreted language which has been used to write lot of popular software, such as :
-
Google
-
MongoDB
-
Netflix
-
Uber
-
Kubernetes and many more.
If an attacker is able to exploit this vulnerability, the attacker can plant backdoor via Command injection or via RCE will affect all the software’s using this version of Go. No public exploit is available for this vulnerability.
1.6 Virsec Security Platform (VSP) Support:
-
-
VSP-Web capability can detect all types of command injection attack and prevent this attack from being exploited.
-
VSP-Host monitors processes that are spawned which are not part of a set of whitelisted process. Any attempt to execute new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
-
1.7 Reference Links:
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


