Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
1.1 Vulnerability Summary
Apache Druid includes the ability to execute user-provided JavaScript code embedded in various types of requests. This functionality is intended for use in high-trust environments, and is disabled by default. However, in Druid 0.20.0 and earlier, it is possible for an authenticated user to send a specially-crafted request that forces Druid to run user-provided JavaScript code for that request, regardless of server configuration. This can be leveraged to execute code on the target machine with the privileges of the Druid server process.
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
The CVSS Base score of this vulnerability is 8.8 High as per NVD.
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
1.3 Affected Version
Apache Druid 0.20.0 and earlier.
1.4 Vulnerability Attribution
This vulnerability is reported by Litch1 from the Security Team of Alibaba Cloud.
1.5 Risk Impact
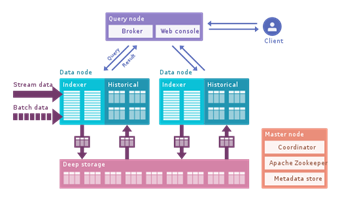
Druid is a column-oriented, open-source, distributed data store written in Java. Druid is designed to quickly ingest massive quantities of event data and provide low-latency queries on top of the data.
Druid is commonly used in business intelligence/OLAP applications to analyze high volumes of real-time and historical data. Druid is used in production by Top 100 technology companies such as Alibaba, Airbnb, Cisco, eBay, Lyft, Netflix, PayPal, Pinterest, Twitter, Walmart, Wikimedia Foundation[10] and Yahoo.
Exploiting this vulnerability will allow an attacker to take over production machines or plant backdoor for exfiltration of critical company and customer information. There are no publicly available exploits.
1.6 Virsec Security Platform (VSP) Support:
-
VSP-Web capability can detect all types of command injection attack and prevent this vulnerability from being exploited.
-
VSP-Host monitors processes that are spawned which are not part of a set of whitelisted processes. Any attempt to execute a new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
1.7 Reference Links:
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


