Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
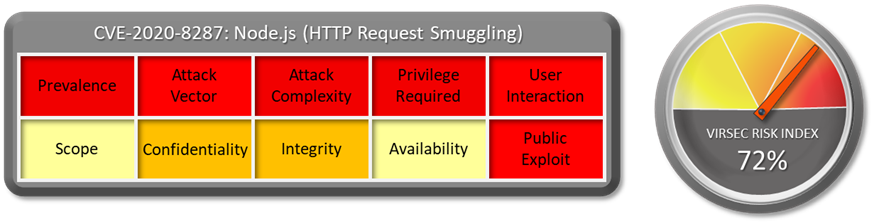
1.1 Vulnerability Summary
Node.js server allow two copies of a header field in an HTTP request (for example, two Transfer-Encoding header fields). In this case, Node.js identifies the first header field and ignores the second. This can lead to HTTP Request Smuggling.
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
CVSS Base score of this vulnerability is 6.5 Medium. CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N
1.3 Affected Version
Node.js versions before 10.23.1, 12.20.1, 14.15.4, 15.5.1.
1.4 Vulnerability Attribution
This vulnerability is disclosed by user “Piao” of HackerOne.
1.5 Risk Impact
Node.js is an application runtime environment that enables using JavaScript for building server-side applications that have access to the operating system, file system, and everything else to be fully functional. Among other server-side technologies, Node stands out with its speed, and intensive data exchange. It is a JavaScript runtime built on Chrome's V8 JavaScript engine. It uses an event-driven, non-blocking I/O model that makes it lightweight and efficient. Node. js can handle many concurrent requests. This is the main reason it quickly became popular among developers and large companies. Some users of Node.js are Netflix, Walmart, UBER, PAYPAL, LinkedIn etc.
HTTP Parameter smuggling allows an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users
A publicly disclosed exploit is available here.
1.6 Virsec Security Platform (VSP) Support:
VSP-Host monitors processes that are spawned which are not part of a set of whitelisted process. Any attempt to execute new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
1.7 Reference Links:
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


