Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides detailed analysis on recent and notable security vulnerabilities.
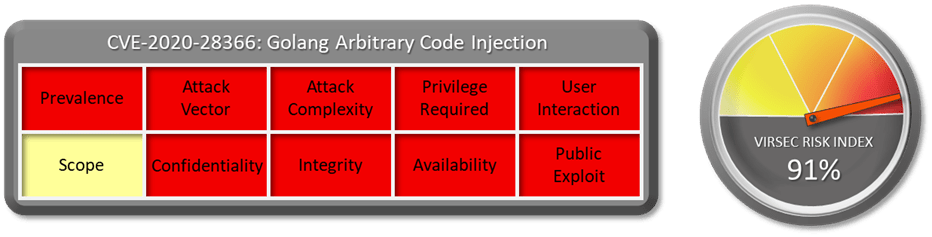
1.1 Vulnerability Summary
The go command may execute arbitrary code at build time when cgo is in use. This may occur when running go get on a malicious package, or any other command that builds untrusted code. This can be caused by malicious unquoted symbol names referred to by the go:cgo_ldflag.
When the Go tool sees that one or more Go files use the special import "C", it will look for other non-Go files in the directory and compile them as part of the Go package. Any .c, .s, or .S files will be compiled with the C compiler. Any .cc, .cpp, or .cxx files will be compiled with the C++ compiler. Any .h, .hh, .hpp, or .hxx files will not be compiled separately, but, if these header files are changed, the C and C++ files will be recompiled. Example usage is as follows: go tool cgo [cgo options] [-- compiler options] gofiles. The -dynimport file option allows arbitrary files to be imported.
Successful exploitation of these vulnerabilities could lead to disclosure of sensitive information, addition or modification of data, or Denial of Service (DoS).
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
CVSS Base score of this vulnerability is 7.5 Critical. (CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H)
1.3 Affected Version
Go 1.14 and 1.15
1.4 Vulnerability Attribution
Imre Rad, Chris Brown and Tempus Ex
1.5 Risk Impact
go get does a lot under the hood, including invoking third-party tools like git and clang in ways that are heavily influenced by package configurations. Ensuring that these invocations are safe is an uphill battle that Go has not quite won yet. Go is a very popular language and is leveraged by many ISV to build their products. For example, NetApp has acknowledged that several of its products are built using go.
An exploit could be constructed easily.
1.6 Virsec Security Platform (VSP) Support:
The Virsec Security Platform (VSP)- This issue is a compile time issue that has the potential to inject malicious code into the original code. If such malicious code were to spawn new malicious processes, thanks to its Application Control capabilities, VSP-Host would be able to prevent maliciously imported files from executing.
1.7 Reference Links:
- https://nvd.nist.gov/vuln/detail/CVE-2020-28366
- https://github.com/golang/go/issues/42559
- https://security.netapp.com/advisory/ntap-20201202-0004/
- https://golang.org/cmd/cgo/
- https://blog.tempus-ex.com/gos-recurring-security-problem/
- https://android.googlesource.com/platform/prebuilts/go/windows-x86/+/studio-master-dev/src/cmd/cgo/doc.go
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities


