Kaspersky’s latest report reveals threats to industrial systems in H2 2018, but underplays real threats its own systems fail to detect
A new Kaspersky update shows nearly 1 in 2 industrial systems bear evidence of attempted malicious break-ins. They say their own (Kaspersky) solutions detected over 19.1K modifications of malware and their Kaspersky Lab ICS CERT identified 61 vulnerabilities in industrial and IIoT/IoT systems. As in prior reports, Kaspersky noted in the vast majority of cases the infection attempts seen were random versus a targeted attack. What they saw most was Trojan malware, detected on just over 27% of ICS computers.
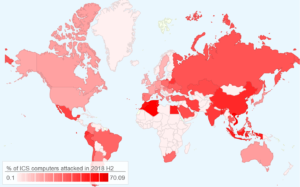
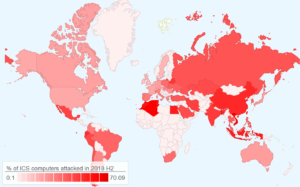
ICS threats by country
Among Kaspersky’s statistics are the following stats per country.
• Countries with the highest proportions of ICS computers on which malicious objects were detected during H2 2018 were Vietnam (70.1%), Algeria (69.9%), and Tunisia (64.6%).
• The most secure countries are Ireland (11.7%), Switzerland (14.9%), Denmark (15.2%), Hong Kong (15.3%), the UK (15.7%), and the Netherlands (15.7%).
• Western Europe (5.1%) is one of the TOP 3 regions based on the percentage of ICS computers on which malicious email attachments were blocked.
Below is a map showing the percentage of ICS computers on which malicious objects were detected in different countries of the world:
Phishing a prominent means of initial attack
Kasperski identifies phishing attacks as the main cyber attack vectors on industrial companies. Phishing emails contain malicious attachments that threaten to compromise or take over office computers as well as network computers within the ICS infrastructure.
However, while phishing is a highly potent and dangerous threat, some real-life attacks show that it’s not always the primary attack vector. A couple significant ICS attacks, such as Triton and Industroyer, were specifically targeted by bad actors.
The WannaCry virus took advantage of an SMB vulnerability in the Microsoft kernel, using EternalBlue and DoublePulsar toolkits and DLL injection to establish a backdoor. And while WannaCry did not specifically target industrial companies, many were struck by it and damaged anyway.
Kaspersky Lab reported on what it could see, but not more critical attacks it couldn’t see
Ray DeMeo, co-founder and chief operating officer at security solution provider Virsec, commented on the limitations of the report:
“The industrial automation space is definitely vulnerable and raising awareness of this is important. However, this report perpetuates outdated models of how to address these advanced security issues and only reports on what perimeter tools like Kaspersky can see – repetitive known malware, used by copycat hackers.
Kaspersky refers to the threat from targeted attacks as a “myth” – this attitude is both naïve and dangerous. Numerically, there are of course more instances of unsophisticated script kiddies running known tools repetitively, but these are easily stopped by the most basic AV tools, along with user training.
The vast majority of damage, disruption, financial loss and fear around industrial security comes from new, targeted attacks that have never been seen and cannot be detected by signature-based tools. Triton, Industroyer, WannaCry, Blackenergy, Greyenegy and others all started as targeted attacks aimed at specific organizations and specific types of ICS systems, and caused tens of billions in damages. These can only be detected and stopped by security tools that guardrail how applications actually execute, as opposed to chasing elusive threats.”
Read full New Insights: Threat Landscape for Industrial Automation Systems in H2 2018 report
Read full Industrial Security Limited In Scope article
*Threat Landscape for Industrial Automation Systems
For more information, visit our Critical Infrastructure Protection page.