The recent Midnight Blizzard saga has shown how threat actors can infiltrate and conduct stealthy attacks that can go unnoticed for a long time. This poses a significant challenge for organizations, as there are no IOCs for EDR vendors to share. However, by adopting a defense-in-depth security solution that provides visibility into server workloads and verifies trust, organizations can protect themselves against known and unknown threats, including those that leverage zero-day vulnerabilities and LOLBin attacks.
Background: On January 12, 2024, Microsoft’s Security Team detected an attack on their corporate systems. They activated processes that included investigation, disruption of malicious activity, mitigation, and denying the threat actor further access. Unfortunately, the threat actor managed to embed itself so deeply in the Microsoft infrastructure that they allegedly have not yet been found.
What is Midnight Blizzard? The threat actor, most recently called Midnight Blizzard, is a group of the Russian government’s spy agencies — namely the SVR and the FSB - whom others have previously named as Nobelium, Cozy Bear, APT 29, Iron Hemlock, UNC2452, StellarParticle, DarkHalo, SolarStorm, and The Dukes. This threat actor primarily targets US and European governments as well as large enterprise platforms that do business with those governments. This same threat actor is credited as the mastermind behind the SolarWinds attack. Interestingly, different cybersecurity vendors cannot agree on a common name for Midnight Blizzard!
How was Microsoft initially infiltrated?
- Initial Infiltration Stage: On January 19, 2024, in their official blog, Microsoft says:
“Beginning in late November 2023, the threat actor used a password spray attack to compromise a legacy non-production test tenant account and gain a foothold, and then used the account’s permissions to access a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions, and exfiltrated some emails and attached documents.”
On January 26, 2024, Microsoft also stated that the legacy servers did not have MFA turned on. This lapse made the threat actor’s task a lot easier.
- Persistence Stage: In the blog mentioned above, Microsoft goes on to say:
“They utilize diverse initial access methods ranging from stolen credentials to supply chain attacks, exploitation of on-premises environments to move to the cloud laterally, and exploitation of service providers’ trust chain to gain access to downstream customers. Midnight Blizzard is also adept at identifying and abusing OAuth applications to move laterally across cloud environments and for post-compromise activity, such as email collection.”
- Data Collection Stage: Having achieved initial infiltration and persistence, the threat actor targeted Microsoft Exchange Online and Microsoft’s corporate email accounts. They bounced through a vast chain of residential proxies to throw threat hunters off the trail.
- Lateral Movement Stage: In its blog of March 8, 2024, Microsoft said that in addition to gaining valuable information from corporate emails, the adversary had also infiltrated Microsoft’s source code repositories and internal systems. The attacks appear to be so pernicious that they are going on to this day, and in fact, the velocity of the password spraying technique has increased tenfold in volume since January 2024.
What has Microsoft learned from this recent attack?
Its blog has identified four significant learnings for Microsoft:
- The landscape of attack tactics is changing: In May 2023, Microsoft published this blog warning that threat actors were increasingly turning to Living-Off-The-Land-Binary (aka LOLBin) attacks that brought the Endpoint Detect-and-Respond (EDR) class of technologies to its knees. Our internal testing with other EDRs confirmed that bleeding-edge cyber attack detection techniques, including AI, show lower efficacy against these kinds of attacks. What makes this starkly evident is that in the end, Microsoft published precise Indicators of Compromise (IOCs) (aka signatures) to address this cyberattack efficacy gap.
Two key takeaways:
-
-
Behavioral monitoring and AI-based algorithms that have long claimed very high efficacy ended up ceding to very specific IOCs, and
-
An accomplished threat actor, leveraging LOLBin techniques, can cut through modern-day EDRs like a knife through butter.
-
Software applications are very predictable. For example, an app that adds numbers will produce the same result today, tomorrow, and even years from now.
- AI-Based Cyber Defense: Microsoft’s Threat Analysis Center (MTAC) is launching and will be working to strengthen its AI systems. Microsoft said,
“While threat actors seek to hide their threats like a needle in a vast haystack of data, AI increasingly makes it possible to find the right needle even in a sea of needles. And coupled with a global network of data centers, we are determined to use AI to detect threats at a speed that is as fast as the Internet itself”.
Microsoft also said,
“Additionally, the speed, scale, and sophistication of attacks creates an asymmetry where it’s hard for organizations to prevent and disrupt attacks at scale. Microsoft’s Security Copilot combines a large language model with a security-specific model that has various skills and insights from Microsoft’s threat intelligence.”
Three key takeaways:
-
-
Cybersecurity providers who have leveraged AI for a long time need to substantially up their AI game,
-
Cybersecurity vendors are not looking for proactive protection for unknown vulnerabilities/ attacks but to detect the attacks as early as possible, and
-
Advanced threat actors such as Midnight Blizzard will routinely mount new and sophisticated threats that will blindside EDRs
-
A legitimate app uses the same set of APIs as a malicious app. No matter how much knowledge of threats the AI has, until it knows the app’s intent, a cybersecurity solution can never reliably detect when code goes rogue.
- Engineering Advances: Microsoft is revamping how software is built and managed throughout its lifetime at Microsoft. The two essential principles in this pursuit are (a) use dynamic SDLC processes whereby not only learnings from the field are incorporated back into the CI/CD pipeline but also more memory-safe languages are used in its products and more secure defaults provided to end users, (b) use hardened identity signing keys to minimize eliminates the danger posed by stolen static tokens.
Three key takeaways:
-
-
Attackers have long been able to insert themselves into communications channels and intercept/ create fake messaging to achieve their objectives,
-
Until all applications adopt the newest identity protection techniques, exposure will continue, and
-
Apps must rotate tokens frequently so that the damage posed by stolen keys is minimal and restricted to a short key-renewal window
-
- Vulnerability Response and Updates: Microsoft plans to leverage AI for code development to reduce the time to release vulnerability patches by 50%. According to a study by Mandiant, the average time between disclosure and patch availability was approximately nine days. Effectively, Microsoft says that the average number of days to release a patch will decrease from nine to four days.
Unfortunately, the problem with vulnerabilities is not with releasing patches faster. A report by Dark Reading claims that it took an average of 38 days for an organization to patch a vulnerability, regardless of its severity level. According to IBM, the Mean Time To Patch (MTTP) is between 60 and 150 days. A 2023 study found that, on average, companies worldwide take between 88 and 208 days to patch cyber vulnerabilities. The exposure on account of unpatched vulnerabilities that enterprises experience is therefore related to patching deficit and not the speed at which Microsoft releases patches.
Key takeaway:
-
-
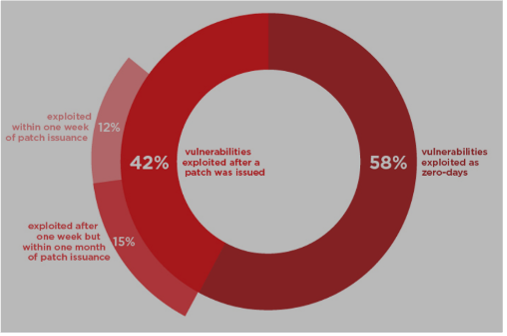
A vulnerability is the initial infiltration pathway into an enterprise’s infrastructure. According to Mandiant, threat actors exploit 58% of vulnerabilities as zero-days. In other words, the Independent Software Vendor (ISV) who produced the software was unaware of the vulnerability. It is also important to note that Microsoft has observed EDRs get easily blindsided if the threat actor leverages LOLBIN Attacks. These two thoughts make it abundantly clear that the threat actor can infiltrate and conduct stealthy attacks, which will go unnoticed for a long time. This further means there will be no IOCs for EDR vendors to share. The enterprise has no recourse against sophisticated attacks that leverage zero-day vulnerabilities for the initial infiltration stage.
-
How do effective security solutions help fend off threat actors like Midnight Blizzard?
-
When you are able to identify files, processes, scripts, and executables running on server workloads, you can establish trust and create a policy to enforce that trust.
-
If you have an intricate understanding of your applications, you can easily distinguish legitimate actions and code from malicious ones and can prevent a threat actor from infiltrating the organization in milliseconds.
-
A default-deny, allow-on-trust approach stops attacks even if the threat actor has obtained access credentials or if it's an unknown attack.
As Microsoft is so painfully learning, once in, threat actors can entrench themselves so deeply that it can be challenging to stop them, especially if they leverage LOLBin attacks.
Conclusion: Despite the efforts of the Microsoft security team, the Midnight Blizzard saga that started in November 2023 shows no sign of abating. Even more importantly, it exposed a severe limitation for EDR solutions — their inability to detect LOLBin attacks. Organizations can protect themselves against attacks like Midnight Blizzard by having a defense-in-depth security solution that provides visibility into what’s running on server workloads and verifies trust, thus defining system integrity. Once that trust has been established, all malicious code can be stopped from ever executing, halting known and unknown threats in milliseconds.
Don't miss our security insights, and subscribe to our blog now.