Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
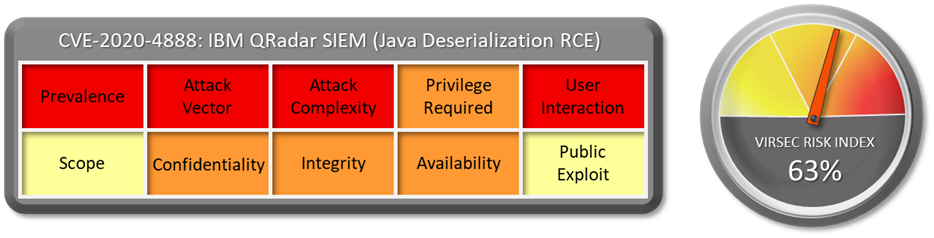
1.1 Vulnerability Summary
IBM QRadar SIEM 7.4.0 to 7.4.2 Patch 1 and 7.3.0 to 7.3.3 Patch 7 could allow a remote attacker to execute arbitrary commands on the system, caused by insecure deserialization of user-supplied content by the Java deserialization function. By sending a malicious serialized Java object, an attacker could exploit this vulnerability to execute arbitrary commands on the system.
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
The CVSS Base score of this vulnerability is 6.3 medium as per IBM and NVD has not provided any score yet. CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L
1.3 Affected Version
IBM QRadar SIEM 7.4.0 to 7.4.2 Patch 1 and 7.3.0 to 7.3.3 Patch 7.
1.4 Vulnerability Attribution
These vulnerabilities were discovered and reported by IBM corporation.
1.5 Risk Impact
IBM QRadar is an enterprise security information and event management (SIEM) product. It collects log data from an enterprise, its network devices, host assets and operating systems, applications, vulnerabilities, and user activities and behaviors. IBM QRadar then performs real-time analysis of the log data and network flows to identify malicious activity so it can be stopped quickly, thereby preventing or minimizing damage to the organization.
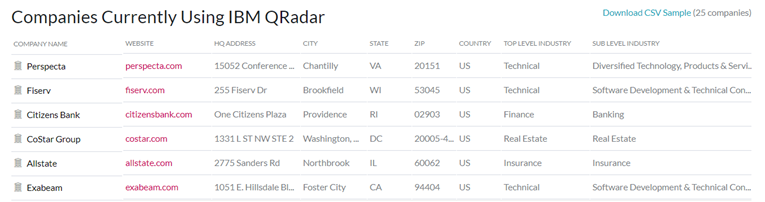
As per this website, IBM QRadar SIEM has more than 8% market share. Some of the top 1000 enterprise customers using this product is as below:
No exploits are available publicly. Any exploit of this vulnerabilities could lead to exposure of all sensitive data that resides on the server via backdoor which could be doing data exfiltration to CnC server.
1.6 Virsec Security Platform (VSP) Support:
VSP-Host monitors processes that are spawned which are not part of a set of whitelisted process. Any attempt to execute new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
1.7 Reference Links:
- NVD - CVE-2020-4888 (nist.gov)
- Security Bulletin: IBM QRadar SIEM is vulnerable to deserialization of untrusted data (CVE-2020-4888)
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


