Going to RSA? Meet with the executive team at Virsec to learn about our latest innovation in server workload hardening, TrustSight!

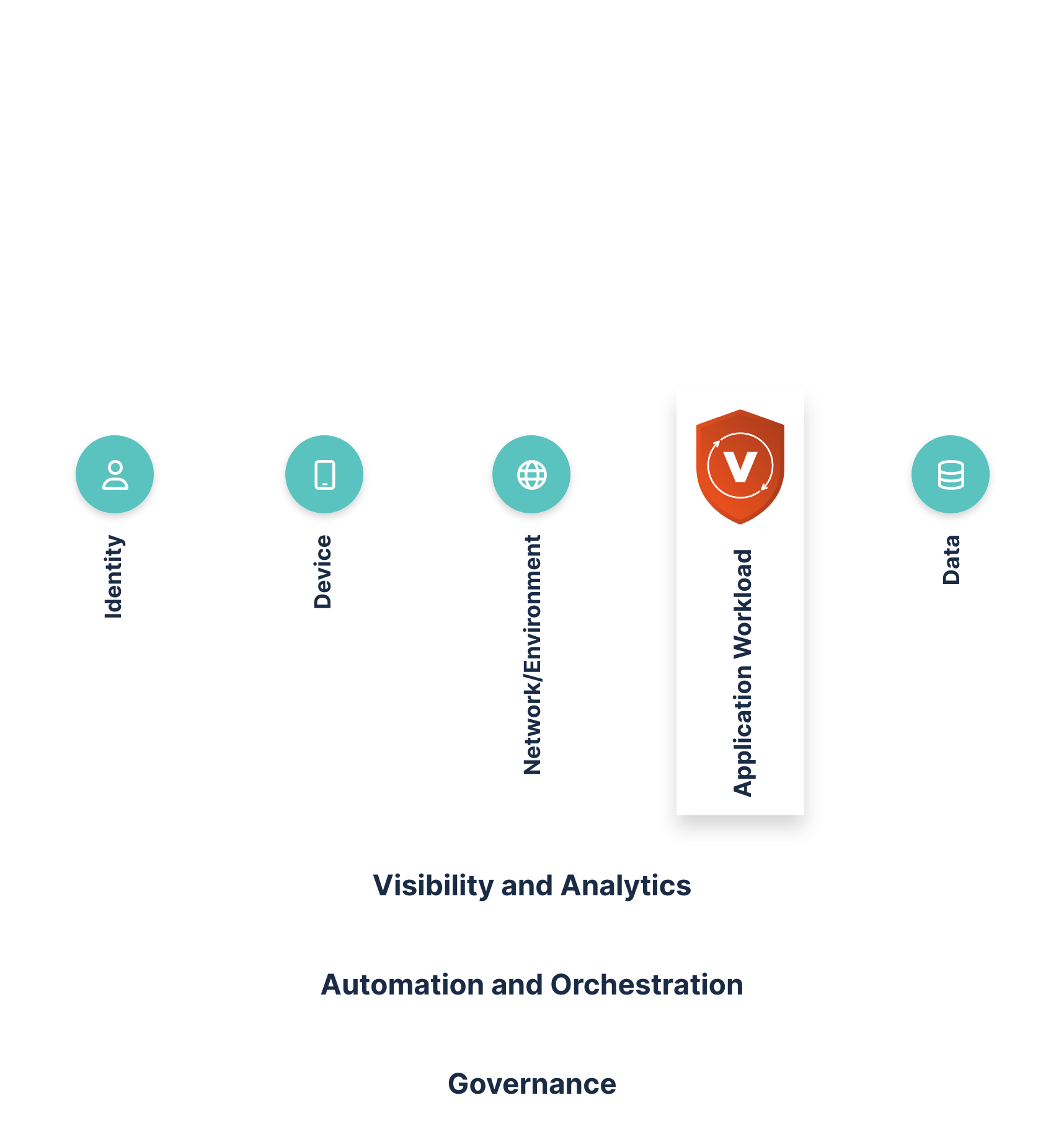
First and foremost, zero trust is a security model that eliminates implicit trust and uses a “verify first, then allow” stance. Most organizations apply this in cybersecurity to identity and authentication, but stop before their applications because the existing solutions claim "Zero trust" yet don't follow the "verify first, then allow" model for application workloads.
Agencies like the Department of Defense and the Cybersecurity and Infrastructure Security Agency (CISA) have expanded their definition of zero trust to encompass more than identity, authentication, and network traffic.
Deny access by default. Every device, user, application/workload, and data flow are authenticated and explicitly authorized using least privilege, multiple attributes, and dynamic cybersecurity policies.”
DoD Zero Trust Reference Architecture - V2 July 2022
Applications and workloads include agency systems, computer programs, and services that execute on premise, as well as in a cloud environment. Agencies should secure and manage the application layer as well as containers and provide secure application delivery.
CISA Zero Trust Maturity Model - Pre-decisional Draft June 2021
Continuous protection of application and host workloads stops cyber criminals and nation-state cyber threats.

Virsec’s unique approach creates a trust-benchmark — a map of known-good application workload behavior, memory processes, files, etc., and leverages this allow-list to ensure that any unexpected processes or workflow activity is stopped in milliseconds. This prevents any modified code, remote code injection or execution, or memory corruption from occurring — effectively eliminating the chance of any zero-day exploits, even in unpatched or legacy environments.
Virsec Map then verifies every executable’s reputation and dependencies, creating a known-good positive security model.
Finally, Virsec Map processes an automated allow-listing, including executable memory mapping to know what’s trusted and what’s not.
Virsec Enforce provides full-time runtime protection of workloads by ensuring only approved and trusted processes, files, scripts, and libraries are used.
Most solutions attempt to stop known bad code and unknown code that looks suspicious, but very few stop everything except what's trusted. Legacy approaches ignore the first principle of zero trust — verify then allow — and open the door to novel malware or zero-days. Virsec, by default, blocks any known OR unknown threat in milliseconds.
