When organizations need to get applications up and running quickly, they turn to cloud infrastructure. The last two years accelerated this strategy as nearly everything went digital. But now cloud users are facing an existential threat.
It is a well-established fact that an unprotected computer left exposed on the Internet, will be attacked in under seven minutes. The presence of unpatched vulnerabilities on an Internet-facing application, very quickly makes the computer unprotected. In 2021 alone, over 28,000 new vulnerabilities were disclosed into vulnerability databases. Approximately 5,800 of these vulnerabilities had publicly available exploits, so even newbie attackers can be dangerous. It is safe to say that most organizations would not have patched these vulnerabilities in the first seven minutes of disclosure. The recent Log4j vulnerability brought this problem into sharp focus.
So, how do you keep your cloud applications secure on an ongoing basis?
Some companies mistakenly assume their cloud provider will protect them from any calamity. Large ISVs have well-endowed design development and QA resources and processes. Despite that, vulnerabilities such as the PrintNightmare and Log4j attacks made it painfully clear that vulnerabilities will continue to escape scrutiny – sometimes for as long as 18 years. Read the disclaimer in your cloud service contract and cyber risk is clearly positioned as a shared responsibility.
Cloud Provider Shared Responsibility Model
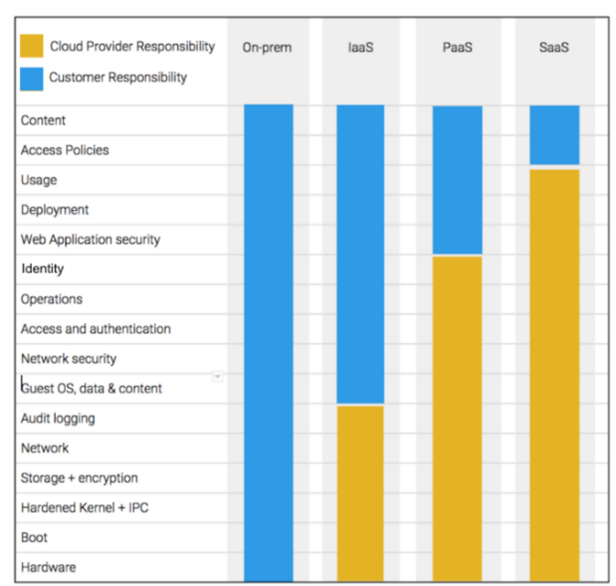
Source: Google
Cloud providers are adept at quickly patching known vulnerabilities which is critical to help mitigate risk, but that isn’t enough. Highly skilled attackers and clandestine organizations in nation states are not exactly rushing to the vulnerability databases to report their findings. Until these vulnerabilities are made public, and a patch is available, the window of exposure remains open.
A game-changing approach
For centuries, the First Principles strategy has been used to deconstruct complex problems into basic elements, and then reassemble them from the ground up to unleash creative thinking and breakthrough solutions. The term was first coined by Aristotle as a way to explain his approach to philosophy. Fast forward 2,000 years and Tesla CEO and SpaceX founder Elon Musk and Netflix CEO Reed Hastings have used the “first principles” decision-making strategy to build companies that disrupt and improve entire industries.
When we apply “first principles” thinking to the challenge of cybersecurity we discover that the tip of the spear of attacks is a vulnerability in an application, not the malware that ultimately triggers malicious actions. So, to achieve better protection we need to shift from following the attacker and the myriad malicious activities they can undertake, to following the code. Think of it this way. Say, you enter 3 + 3 into a calculator. The answer is always 6 – today, tomorrow and even five years from now. However, if an attacker were to switch from the + key to the x key, suddenly the answer becomes 9 which produces a dramatically different result.
The learning from this example is that code is deterministic and will execute the same way today, tomorrow and even five years from today.
Looking at cybersecurity, developers use code to predetermine how the application operates. A vulnerability in an application provides a pathway for the attacker, allowing them to seize control and unleash code of their choosing. Identifying this precise event of transfer of control from developer code to attacker-influenced code is key to stopping cyberattacks. When we continue to apply first principles thinking to other aspects of this complex challenge, including how applications are written, the points at which attackers can seize control (host, memory, and web), the fact that code is built modularly, and the challenges of making such a solution usable and reliable, we arrive at a new, comprehensive approach to cybersecurity: deterministic protection.
Eliminate ambiguity
Deterministic protection involves understanding what the application is predetermined to do, and immediately stops unauthorized code from running on the application. It protects against all types of attacks, including zero days. And because you aren’t chasing attacks, the entire concept of patching and updating protections on a case-by-case basis is moot. When a deterministic protection control operates in runtime it can see a tremendous amount of detail. Conceptionally, it’s like having a GPS on all the time and even a small deviation from the intended path will generate an immediate warning. Deterministic protection triggers protection actions as soon as the application veers off course. With pinpoint accuracy you can stop an attack in progress – disclosed or undisclosed – before damage is done.
With more complete and reliable protection you don’t have to worry about shared responsibility or deal with finger-pointing. Organizations and cloud providers have peace of mind and security response becomes obsolete because attacks are stopped before the attacker can inflict any damage. What’s more, for IaaS customers, which Gartner estimates to be one of the highest growth segments in 2021, deterministic protection can instill greater confidence to move more services to the cloud and also entice fence-sitters. Everyone wins. It’s what the cybersecurity industry and the people it serves need right now.





