Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities (CVEs).
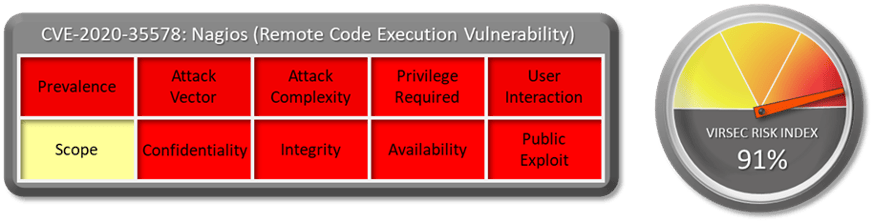
1.1 Vulnerability Summary
An issue was discovered in the Manage Plugins page in Nagios XI before 5.8.0. Because the line-ending conversion feature is mishandled during a plugin upload, a remote, authenticated admin user can execute operating-system commands.
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
The CVSS Base score of this vulnerability is Not Available currently.
1.3 Affected Version
Nagios XI before 5.8.0.
1.4 Vulnerability Attribution
This vulnerability is disclosed by Nagios.
1.5 Risk Impact
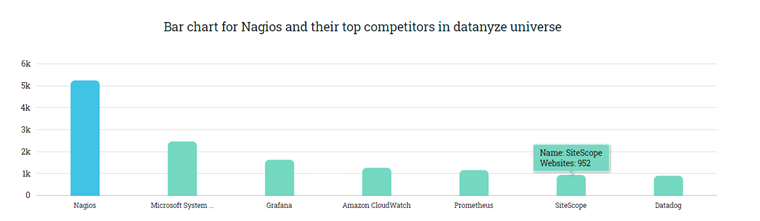
Nagios, is a free and open-source computer-software application that monitors systems, networks and infrastructure. Nagios offers monitoring and alerting services for servers, switches, applications, and services. It alerts users when things go wrong and alerts them a second time when the problem has been resolved. As per this website, Nagios is market leader in IT infra monitoring and has 20% percent market share that manages close to 5250 Domains.
Exploiting this vulnerability can lead to attacker planting a backdoor and affecting the entire organization leaking out important software codes and information.
Exploit is available in public domain here.
1.6 Virsec Security Platform (VSP) Support:
VSP-Host monitors processes that are spawned which are not part of a set of whitelisted process. Any attempt to execute new command or unknown binary would be denied by VSP-Host’s Process Monitoring capability.
VSP-Web has capability that can detect all types of OS command injection attack and prevent this attack from being exploited.
1.7 Reference Links:
- NVD - CVE-2020-35578 (nist.gov)
- Nagios XI 5.7.x Remote Code Execution ≈ Packet Storm (packetstormsecurity.com)Security Disclosures - Nagios
- IT Infrastructure Monitoring Market Share Report | Competitor Analysis | Nagios, Microsoft System Center Operations Manager, Grafana (datanyze.com)
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Jump to: List of CVE Vulnerabilities
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


