No Quick Fix for Chip Flaw in Sight;
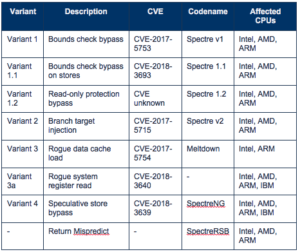
A year following the revelation of Spectre and Meltdown chip flaws, a new flaw – Spoiler - has been discovered that affects all Intel chips. The flaw occurs because of how Intel chips perform speculative execution in order to increase CPU performance. The flaw affects all Intel chips going back to the first generation of Intel core processors, with any OS. The flaw is not present in AMD or Arm processors.
Attackers Can Leverage Spoiler to Get to Secret Information
Speculative execution is the same element also used in Spectre and Meltdown attacks, but Spoiler leverages it differently. Spoiler uses a weakness in the Intel CPU, targeting the Memory Order Buffer in the processor, which manages memory operations and is aligned functionally with the cache. An attacker can use Spoiler to abuse speculative execution to access secret information from memory. Secret information could include a system’s virtual address mapping to physical memory address.
Unlike Spectre v2, Spoiler is not a speculative execution side-channel attack, which could leak secrets like passwords. But Spoiler does aid and abet other known memory-leaking attack techniques, such as Rowhammer described below, and classic side-channel attacks in their attacks.
Researchers have described how the attack is different from Spectre in their report: SPOILER: Speculative Load Hazards Boost Rowhammer and Cache Attacks*. Intel has already been working to mitigate Spectre and similar attacks like SplitSpectre. But again, the root cause behind Spectre and Spoiler differ.
Spoiler depends on "a novel microarchitectural leakage, which reveals critical information about physical page mappings to user space processes." Researchers say, "The root cause for Spoiler is a weakness in the address speculation of Intel's proprietary implementation of the memory subsystem, which directly leaks timing behavior due to physical address conflicts. Existing Spectre mitigations would therefore not interfere with Spoiler."
Limited instructions can exploit the leakage. This compromise can happen in all Intel generations from the first of Intel Core processors, separate from the OS. It can also occur in virtual machines and sandboxes.
The Rowhammer Class of Exploits Usurps the Chip Flaw
A class of exploits called Rowhammer takes advantage of the hardware design flaw in modern memory cards. The Rowhammer exploits, discovered in 2014, carry out rogue bit-flipping in memory chip. For the most part, the attacks have been theoretically carried about by analysts with no known attacks occurring in the wild to date.
The Rowhammer attacks are also similar to Spectre and Meltdown. A Rowhammer attack works against ECC memory and could alter DDR3 and DDR4 memory cards. An attack could also be performed via JavaScript via the web without requiring physical access to a computer or through local malware. Other means of attack were demonstrated by analysts as well.
Most noteworthy is that analysts found that Spoiler enhances Rowhammer attacks. The access Spoiler gains to secret information can accelerate reverse-engineering by a factor of 256 times, as well has have similar turbo-charging effect on JavaScript web attacks.
Error-Correcting Code (ECC) memory--used in RAM--mitigates Rowhammer. But researchers have shown the ECC mitigations could be bypassed in DDR3 and possibly DDR4, if three simultaneous bit flips are triggered.
Common Vulnerabilities and Exposures (CVE) Assigned, but No Patch
Intel finally posted an official security advisory in response to the recently revealed Spoiler attack, CVE-2019-0162. Intel ranks its severity score as a 3.8 out of 10. No patch will be forthcoming and perhaps the low score is an indication as to why. The low score is likely because attackers need authenticated access to the hardware, and other mitigations reduce the likelihood of attack success.
No New Solutions or Intel Chip Coming for Years
Per researchers, Intel confirmed receipt of their findings on December 1, 2018. Researchers noted that for JavaScript-based Spoiler attacks via a website, browsers could mitigate Spoiler attacks by removing accurate timers. Yet, removing all timers could be impractical. Also, Intel won't be able to mitigate and fully address the problem of Spoiler exploits using software or hardware. Any hardware mitigations that could address the issue would almost certainly result in a drain on CPU performance.
Daniel (Ahmad) Moghimi, one of the research paper's authors, stated he doubts Intel will be able to patch the issue in the memory subsystem within the next five years. "My personal opinion is that when it comes to the memory subsystem, it's very hard to make any changes and it's not something you can patch easily.”
Sources:
*Research report, “SPOILER: Speculative Load Hazards Boost Rowhammer and Cache Attacks” Researchers from Worcester Polytechnic Institute, Massachusetts, and the University of Lübeck in north Germany https://arxiv.org/pdf/1903.00446.pdf
2. https://www.zdnet.com/article/rowhammer-attacks-can-now-bypass-ecc-memory-protections/