Virsec Security Research Lab Vulnerability Analysis
The Virsec Security Research Lab provides timely, relevant analysis about recent and notable security vulnerabilities.
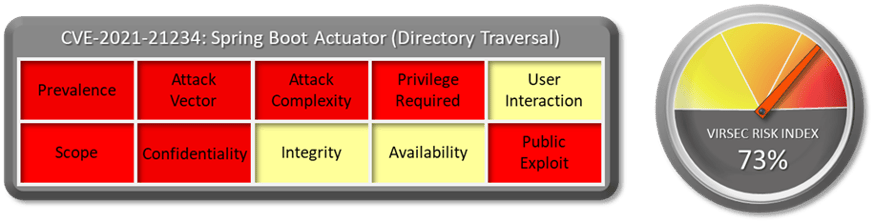
1.1 Vulnerability Summary
The nature of this library is to expose a log file directory via admin (spring boot actuator) HTTP endpoints. Both the filename to view and a base folder (relative to the logging folder root) can be specified via request parameters. While the filename parameter was checked to prevent directory traversal exploits (so that `filename=../somefile` would not work), the base folder parameter was not sufficiently checked, so that `filename=somefile&base=../` could access a file outside the logging base directory).
Watch the video to learn more about this and other important vulnerabilities.
1.2 CVSS Score
NVD Base score of this vulnerability is 7.7 High. CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
1.3 Affected Version
Spring Boot Actuator Log View before version 0.2.13
1.4 Vulnerability Attribution
This vulnerability is fixed by user “lukashinsch” in Git Hub.
1.5 Risk Impact
In short, Spring Boot Actuator is one of the sub-projects of Spring Boot, which adds monitoring and management support for your applications running in production. It exposes various HTTP or JMX endpoints you can interact with. Spring Boot is an open-source Java-based framework used to create a Micro Service. It is developed by Pivotal Team and is used to build stand-alone and production ready spring applications.
If a web server or web application is vulnerable to directory traversal attack, the attacker can exploit the vulnerability to reach the root directory and access restricted files and directories. An attacker may use directory traversal to download server configuration files, which contain sensitive information and potentially expose more server vulnerabilities. Ultimately, the attacker may access confidential information or even get full control of the server.
An exploit is not publicly available but given the disclosure, it is very easy to construct one.
1.6 Virsec Security Platform (VSP) Support:
VSP-Web can block directory traversal attacks deterministically.
1.7 Reference Links:
Download the full vulnerability report to learn more about this and other important vulnerabilities.
Do you have a request for a vulnerability Virsec Security Research Lab to explore? Let us know!


