A business model should be flexible, profitable, and able to adapt to changing conditions, competition, and any adverse conditions in order to continue building revenue. As such, ransomware efforts are a highly successful business and becoming increasingly so week by week. Ransomware operators have become very adept at modifying their modus operandi to maneuver around organizations’ security defensives and outwit software. They’ve even mastered the skill of recruiting legitimate tools and applications to become part of their twisted machinations.
Cyber criminals have been increasing their ransoms, – Ryuk is especially known for going after organizations with deep pockets. Ryuk and Sodinokibi are now collecting average ransomware payments of $111,000. As the lucrative nature of this business draws growing numbers of malware operators, malicious code on the black market is also increasing rapidly – it’s big business on the dark web. It’s not only popular, it’s not expensive and easy to use.
As different buyers purchase the malware, variants emerge, making it easier to escape detection by security products. Many of these products can no longer recognize malware as malware.
For would-be perpetrators who don’t want to produce ransomware variants or carry out the attacks themselves, the dark web offers plenty of help for hire. So the business model is complete – a plethora of products that are adaptable to changing scenarios with affordable, full-service 24x7 support. Barring its illegal status, ransomware-as-a-service (RaaS) would be a practically perfect business model. For criminals who don’t mind the illegalities, it's a money-making machine.
The Expanding Landscape of Ransomware
Ransomware in 2020 is building off its strong year in 2019. In the first quarter of 2019, ransomware attacks rose 118% over the prior year, according to a McAfee report. And even though the overall count of attacks by Q3 of 2019 was slightly less than in 2018, ransomware strikes against cities, schools, hospitals, and public organizations rose significantly. That trend continues into 2020.
Online Shopping Presents Variety of Offers for Ill-Intentioned RaaS Buyers
Thanks to the great success threat actors are having, more ransomware groups are emerging. Would-be users have a wide selection of ransomware packages for sale on the dark web’s black market. It’s a lot like buying software the regular way, complete with add-ons, support, and payment plans, except the purchase is for a criminal product for criminal purposes.
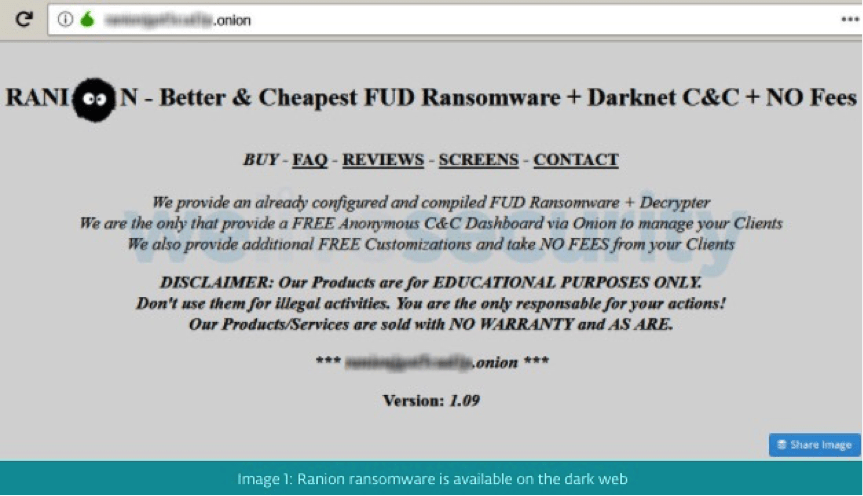
One such package is called Ranion, with monthly and yearly payment subscriptions. One of their ads looks like this:
Figure 1: Ranion ransomware ad on the dark web*
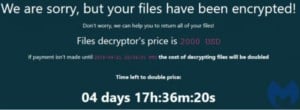
Prices range from $120 per month and $900 per year on the low end, up to $1900 per year if you add additional ransomware executable features. Buyers also have the payment option to receive the malware and C&C server for free in exchange for handing over a cut of the expected ransom payments from upcoming victims.
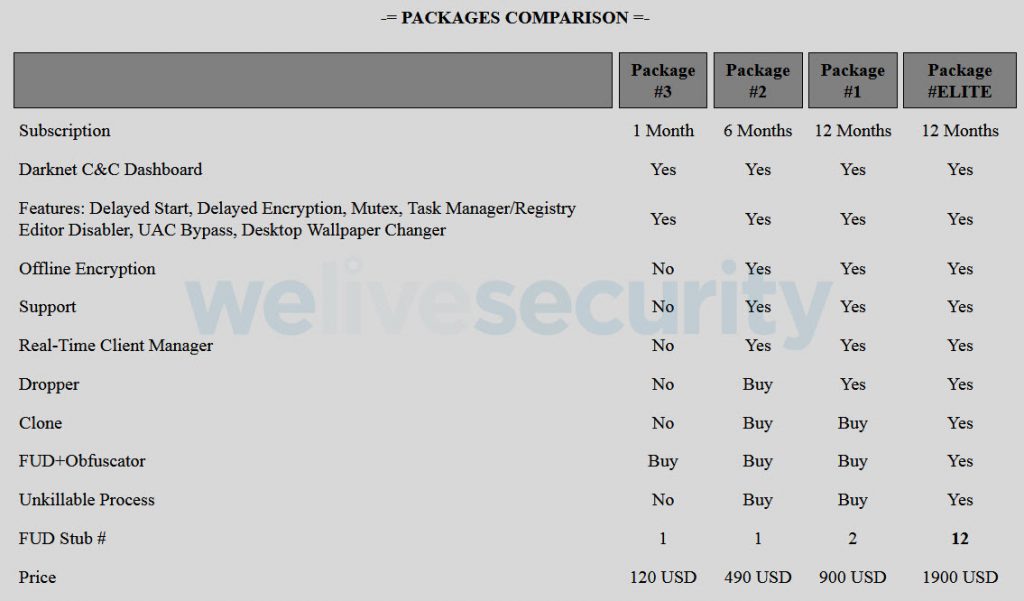
Figure 2: Ransomware packages on the dark web**
Once a purchase is made, then the strategy can be developed as to which victims to target and the best way to target them – phishing email campaigns, exploiting server vulnerabilities, and so on.
Netwalker Ransomware Exploits
Netwalker is an example of RaaS ransomware which first appeared in September of 2019. Numerous types of businesses have been attacked by Netwalker, and known by names such as Mailto and Koko, it’s been used lately in campaigns disguised as health alerts about COVID-19. On March 16, the Illinois Champaign -Urbana Public Health District (CUPHD) website was attacked and brought down, blocking employees from files. The interruption was serious enough for the FBI and Dept of Homeland Security to get involved.
On March 18, BleepingComputer through an article in their web portal asked the NetWalker operators if they would be targeting hospitals. They said they would not, in their response below.
"Hospitals and medical facilities? Do you think someone has a goal to attack hospitals? We don't have that goal - it never was. It coincidence. No one will purposefully hack into the hospital."
Toward the end of March, several additional ransomware groups (Maze for one) promised to refrain from going after medical facilities during the COVID-19 health crisis. Some threat actors said they would not intentionally go after healthcare organizations but if one were accidentally hit, they would offer a discount in assisting. Attacks on medical sites have still occurred. (See our blog Maze & Other Ransomware Groups Say They Won’t Attack Hospitals During COVID-19 Outbreak–But How Trustworthy Is Their Word? )
Netwalker Ransomware Available as RaaS
When executed, NetWalker, aka Mailto, uses an embedded configuration that includes a ransom note, ransom note file names, and various configuration options. Netwalker spreads either by a Visual Basic Script (VBS) script sent as an attachment in a phishing email with a malware-embedded link (which is how the recent Coronavirus-related attack above occurred). The malware can also propagate through an executable file spreading through the network after a user has inadvertently activated it.
In March of 2020, the ransomware group under the user alias of Bugatti, made the Netwalker RaaS model available to cyber criminals.
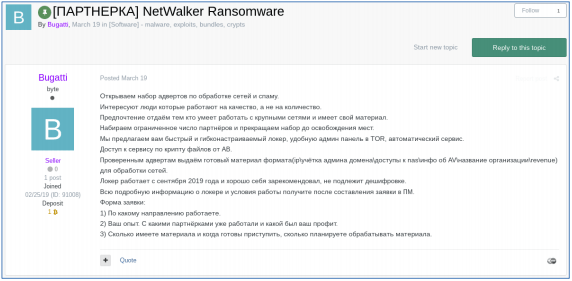
Figure 3: NetWalker Ransomware, Bugatti, RaaS model. Source***
English translation:
[PARTNER] Netwalker Ransomware We’ve opened a set of advertisements to process networks and spam. Interested in people who work towards quality, not quantity. We prefer those who can work with large networks and have their own material. We recruit a limited number of partners and stop recruiting until there are openings. We offer fast and flexible ransomware, an administration panel in TOR and automatic service. Access the service through encrypted files from AV. For verified ads, we deliver prepared material (IP \ admin domain account \ NAS access \ AV information \ organization name \ revenue) for network processing. The ransomware has been operating since September 2019 and has proven itself, it cannot be deciphered. You will receive all the detailed information about ransomware and working conditions after compiling the application in the private message.
Request form:
1) What direction are you working in?
2) Experience. What affiliate programs have you worked with and what were the benefits?
3) How much material do you have? When are you ready to begin? How much of the material do you plan to process?
NetWalker RaaS Model translation; Source****
NetWalker execution plays out in four stages:
- Malicious code impacts Windows libraries
- The executable extracts encryption parameters and ransom instructions from the ransomware configuration file
- Variable initialization begins
- File encryption takes place
Snapshot copies of data are obtained and removed before encryption, preventing backup recoveries of encrypted files. This is done using vssadmin.exe.
As files are encrypted, a unique 6-character ID is generated that becomes part of the extension of the encryption files. It also becomes part of the ransom note.
<SYSTEM32>/vssadmin.exe delete shadows /all /quiet
<SYSTEM32>\vssadmin.exe delete shadows /all /quiet
If you happen to be the unfortunate victim, the following chilling message appears on your screen.
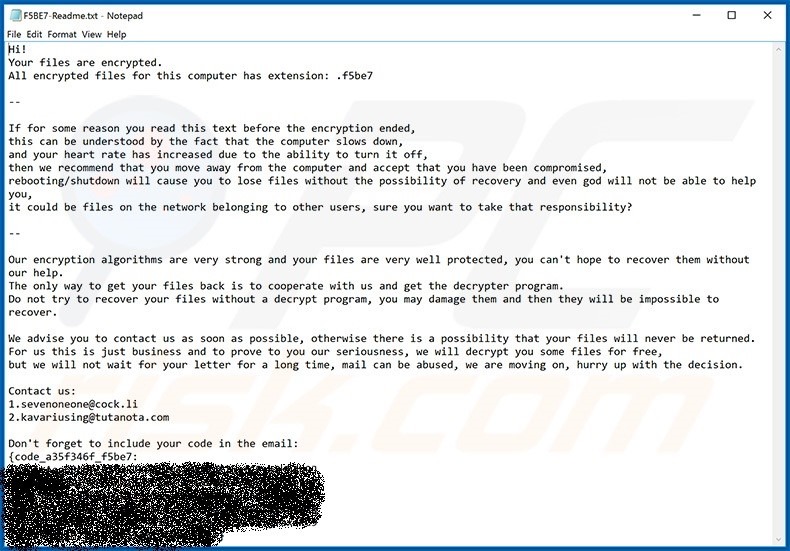
Figure 5: Netwalker’s ransom note and encryption notification; Source: PCrisk
While RaaS May Be Cheap to Buy, It’s Not Cheap to Experience
When a ransomware or cyber attack occurs, the costs are significant and broad. In the immediate moments after an attack is realized, an organization faces the big question of whether or not to pay the ransom. Clearly, some do, contributing to the growing popularity of the RaaS business and despite FBI and DHS advice to the contrary. However, a desperate organization may choose to cooperate with the data-napper’s terms in an effort to get their data and operations back on track as soon as possible.
But whether or not the ransom is paid, additional expenses in the aftermath include getting operations back online, restoring and recovering any damaged data, lost time and business, damage to company reputation, paying third-party experts to assist in forensics and attack analyses, any new security technology needed and possible fines and lawsuits, to name some likely expenses.
In 2018, a post from Cybersecurity Ventures predicted cybercrime costs to the world would double from $3 trillion in 2015 to $6 trillion by 2021.
Taking Defensive Steps Against Ransomware
Organizations can take steps to avoid being a RaaS victim.
Businesses must always be on high alert, especially during this global health crisis where cybercriminals are using increasingly manipulative exploits and businesses are adopting more remote practices. Some organizations are using this time to be more aggressive in revamping their security strategy.
What Can Businesses Do to Protect Themselves from Ransomware and Other Cyber Threats?
- Follow best security practices
- Educate employees about phishing – this may be the best preventative measure you can take
- Enable two-factor authentication on network devices and systems
- Follow a password management policy that enforces regular updates with strong password requirements
- Ensure your third-party vendors follow your security standards
- Implement a reliable backup and recovery system, protected from network access
- Protect applications and memory
Questions to Consider About Your Security Posture During COVID-19 and Beyond
- How effectively are you protecting process memory? NIST and Gartner recommend greater protection is necessary.
- What approaches are you using to ensure the operational integrity of enterprise applications, thus preventing injections that cause applications to perform unexpected or malicious operations?
- How effective are your security tools? Discuss this especially if you are overwhelmed by alerts daily.
- How much effort is required to identify evolving threats?
- What protections are in place to stop threats that have already reached the host server?
Virsec’s Unique and Effective Application, Runtime and Memory Protection Stands Up to Ransomware
Virsec takes a unique approach to guard-railing applications and countering a broad spectrum of cyber attacks, including ransomware attacks. Specifically, Virsec Security Platform provides:
- Protection of application workflows, processes, file systems, libraries, memory and more at runtime
- Precise attack remediation and automation early in the attack cycle without need for expert analysis or machine learning
- Deterministic threat detection based on request deviations initiated by malicious code, remote hackers, files and trusted processes no matter the ways attacks originate.
Learn more about Virsec from the resources below.
Further Resources:
- 2-Minute Virsec Video
- White Paper: Making Applications Truly Self-Defending
- Organizations Especially Vulnerable as CyberAttacks Exploit CoronaVirus OutBreak
- Virsec Newsletter
Relevant Virsec articles:
Enabling Cyber Resilience During COVID-19 Crisis
As Pandemic-Related Traps Spawn Cyberattacks, How Ready Are You?
Sources:
https://www.incibe-cert.es/en/blog/netwalker-ransomware-analysis-and-preventative-measures
https://technologyadvice.com/blog/information-technology/cybersecurity-trends-2020-ransomware/
https://www.cynet.com/blog/netwalker-ransomware-report/
https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/
Figure sources:
*, **welivesecurity.com
***, **** El Mundo news
***** PCrisk