What Happened
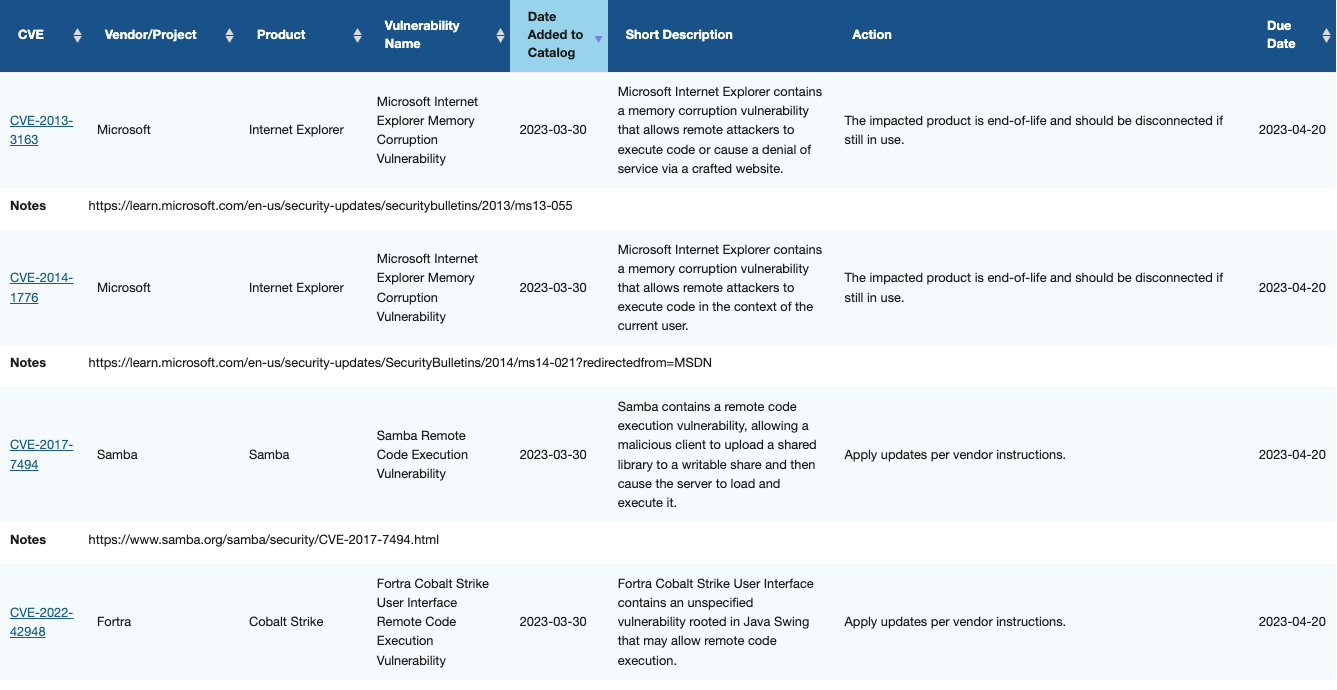
On Wednesday, November 3rd, the Cybersecurity and Infrastructure Security Agency (CISA) issued a directive that orders all federal and executive branch departments and agencies to patch a series of known exploited vulnerabilities as cataloged in a public website managed by CISA.
This new directive changes the CISA's strategy of vulnerability management for federal agencies. Instead of only focusing on vulnerabilities that carry a specific CVSS score, CISA is targeting vulnerabilities for remediation that have known exploits and are being actively exploited by malicious cyber actors.
The directive establishes a CISA-managed catalog of known exploited vulnerabilities that carry significant risk to federal enterprise and establishes requirements for agencies to remediate any vulnerabilities included in the catalog. Approximately 200 vulnerabilities from 2017-2020 and 90 from 2021 make up the initial catalog. CISA will regularly update the catalog with new known exploited vulnerabilities that meet specified thresholds.
CISA wants all vulnerabilities disclosed this year to be patched by this Wednesday, November 17, while patches for older vulnerabilities can be applied till May 3, 2022.
Will it Solve the Problem?
There were 18,358 new cybersecurity vulnerabilities, or Common Vulnerabilities and Exposures (CVEs) identified in 2020; 10,342 of them were classified as “critical” or “high severity”. That’s about 28 critical vulnerabilities every day of the year.
In a recent interview about the new directive, CISA Director Jen Easterly remarked, “We have to do things differently. In many ways, the status quo [of security] is unacceptable.” Closing the gaps in protection is always a good idea and I find no fault with the Agency’s attempt to raise awareness on the subject.
There are, however, two areas of glaring concern:
-
The first is that industry and government have been talking about patching since the dawn of time. Well, just about.
-
The second is a tad more insidious: adversaries appear to have maneuvered around and, in some cases, within the patching paradigm. REF: the devastating SolarWinds hack, which actually started with a poisoned patch.
Key Questions
-
Are we any safer by patching 200 critical vulnerabilities?
-
In light of the fact that the average time it takes to fix critical cybersecurity vulnerabilities has increased from 197 days to 205 days, is November 17 a realistic target for federal agencies?
-
Is patching going to end the current cyber crisis in which we find ourselves?
And then there’s the technical debt most agencies face. That is, old commercial or government software applications that are no longer supported with security updates.
As hard as it might be to admit, the attack landscape across government remains ripe with opportunity. Beyond the old unidentified and un-patchable applications in question, there are a host of other breach methods including fileless attacks, remote code execution (RCE) and “0-days” as zero-day threats are often called, that exploit vulnerabilities without going through traditional malware routes.
Deterministic Protection
In order to fully protect the application—with bugs and outdated versions included—we must fully understand the application from the inside out.
Traditional methods of ‘kernel-hooks’ and monitoring system calls is clearly not enough as this method attempts to wrap the outside of the software but still lacks the ability to absolutely interdict any threat from the inside of the application.
Case in point:
The best-of-breed EDR/EPP vendors boast a “dwell time” (that is, the amount of time the adversary is in your network before you figure out that they are there) of 36 minutes.
The average ransomware attack takes roughly 3 seconds to execute. SolarWinds was a two-step process and therefore took nearly three times longer: 8 seconds.
Virsec’s deterministic approach to protection safeguards the application from the inside regardless of the source or type of threat. And we do it within milliseconds. Enough time to fully interdict any cyber threat in an automated fashion with no application drag or performance hit, no heuristics, AI or machine learning modeling, signatures, indicators of compromise or attack. This means zero dwell time.
Pivoting from today’s probabilistic countermeasures to complete, deterministic protection might seem like an aspirational goal, but it’s real. Full, automated application protection is needed across government—and it is now possible today.