Dark Reading, SC Magazine, Security Week, ISBuzz, May 4, 2018, with comments by Satya Gupta;
Researchers have discovered 8 new versions of the processor vulnerability
Spectre has rebounded with eight new varieties, forcing CPU chip manufacturers to tackle a new barrage of speculative execution vulnerabilities first made known to the public in early January this year.
The discovery was reported last week by www.heise.de, a German security website.
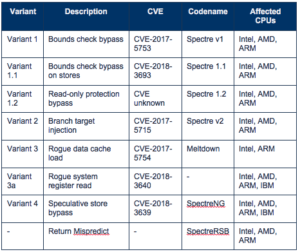
The 8 flaws, called Spectre Next Generation (Spectre-NG) are like the original ones and post vulnerabilities if not patched. The flaws affect Intel chips, at least some ARM and possibly AMD chips.
Four of the Variants Are High Risk - Threatening Virtual Machines (VMs)
Of the 8 new variants, 4 are considered “high risk” and 4 “medium risk.” The vulnerabilities can be exploited by attackers, allowing them to steal sensitive information through a side-channel attack. The process leverages a less secure application to read the memory of another application that’s more secured.
But one aspect this time is considerably more threatening than the previous. Now, it’s believed attackers could go much farther, using the exploit to first attack a virtual machine (VM) and then use that VM as a means to attack the host system and other (VMs) on the same server. With this access, the malicious invasion could read data from the cache of another VM or the hypervisor. The danger for cloud-based services, hosts and servers is particularly high and the possibility of this access increases the chances of a serious breach.
Intel has indicated a plan to release patches in two stages, one this month (May) and the second in August. Microsoft is said to also be developing patches for its Windows updates versus in the form of microcode updates. Both software and firmware updates may be needed.
Satya Gupta, CTO and co-founder of Virsec, is not surprised that new variants of the Spectre attack have emerged.
"It's almost inevitable that new variants of Spectre [would] emerge," said Satya Gupta, CTO and co-founder of Virsec, in comments. "Now that the core vulnerabilities of speculative execution have been publicized, many well-funded hacking groups globally are racing to find new ways to exploit them. These are advanced attacks exploiting small, but repeatable flaws that skip important security controls in literally billions of processors. While not all applications will be vulnerable and some compensating controls will be effective, the attackers are relentless and will continuously search for cracks in other defenses that allow Spectre to be exploited."
Gupta describes the issue. "The basic problem is that, as part of the operating system, we've taken great pains to isolate the memory space of process 1 from the memory space of process 2. This security domain is destroyed by the time you get into the cache," says Satya Gupta, CTO and co-founder of Virsec. That domain destruction is already in process by the time Spectre exploit code executes, though, because of the way that Spectre operates.
Gupta says the ultimate fix to the problem involves a change to one of the processor's core components. "The smallest possible part to change is the instruction cache," he says. "It's agnostic now and it loses the linkage between process and instruction. The processors need to have an idea of which process is executing — memory isolation is really important."
Even more vulnerabilities have also been uncovered by Nvida and Princeton researchers, bringing the total to 13. More are expected. Read our blog to learn what you can do to protect yourself or visit our Spectre Solved resource page.
Read full articles:
Read full Dark Reading Spectre Returns with 8 New Variants article
Read full SC Magazine Ghosts in the Machine article
Read full Security Week Intel Working on Patches for 8 New Spectre-Like Flaws: Report article
Read full 8 New Spectre Variant Vulnerabilities Discovered article