Just because you close your eyes to the matter doesn’t mean it will go away. Yet, as well spoken of in the media, many people are sticking with their “see no Spectre” approach and keeping their fingers crossed. With the first wave of news and hype, a patching frenzy was ignited, but attention quickly shifted elsewhere. The latest variant in the chain of exploit methods, SpectreRSB (attack on return stack buffer), was announced this past week, reminding us both of the gravity the CPU flaw poses if left unchecked, and that this problem may never go away.
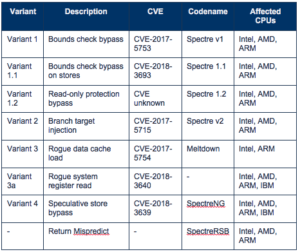
Spectre is a serious matter that we learn more and more about almost daily. Unpatched, it leaves systems and services of all types vulnerable to skilled attackers in ways we never considered threatening. An exploit of this flaw is terrifying at best. The chip-level flaw could allow attackers to steal passwords, customer data, IP and more in the runtime memory of programs, running on a victim’s machine – areas that attackers should not be able to exploit. Furthermore, the flaw opens the door to broader attacks and total system compromise. The latest variant uses a call instruction on x86, which allows an attacker to push a value to the return static buffer so that the return address for the call instruction no longer matches the contents of the return stack buffer. This subsequently allows the attacker to execute a payload gadget (code injected) in the victim’s memory. Execution of foreign code can have devastating effects on services and the organization – service disruption, data theft, fraud and more.
The worst thing about the Spectre flaw is that you will likely not know your system has been compromised until it is too late. Since the vector targets deep within code functions (at the hardware and memory level), conventional application visibility and threat monitoring solutions offer no defense. It also appears that no Spectre patches currently offered by Google or Intel can stop this new Spectre variant. What will likely be required are microcode updates to prevent speculative execution through the RSB, or implementing RSB refilling upon entrance to protected areas in memory. However, microcode updates are risky and generally avoided by users, and the performance hits may be significant.
Today many organizations are struggling with patching all servers and systems vulnerable to known Spectre exploit methods, not to mention new variants. Each vulnerability requires its own Spectre patch to be installed on servers, OS’s and microcode. Thus, patching each variant remains a headache and something that is just not practical. Given this, as Willy Leichter, VP Marketing at Virsec, mentions in his recent Spectre Will Haunt Us for a Long Time article, “Business must of course go on, but ignoring elephant-in-the-room threats like Spectre and Meltdown is never wise. Solutions are emerging that look deeper into processor-caching and memory usage, as are those that selectively limit speculative execution without recompiling code or hobbling performance. The ongoing effort to replace processors will help, too.”
SPECTRE VARIANTS THAT THREATEN YOUR BUSINESS SERVICES

Server-side Spectre and Meltdown attack defense from Virsec
Organizations that have deployed Virsec Security Platform for additional application defense, are uniquely protected against Spectre exploits, without changes to hardware, software, kernel or microcode. Its Trusted Execution™ technology preemptively patches vulnerabilities at the binary level to minimize risk and prevent advanced memory-based threats, fileless malware, and unknown or zero-day attacks in real time. The technology employs a deterministic approach to threat detection and automates protection, preventing efforts to tap into application memory and leak data, or misdirect functions and application process flows. It essentially renders all Spectre variants useless at first attempt, even SpectreRSB. Additionally, customers also benefit from protection against cartographic operations on kernel memory commonly associated with Meltdown.
Virsec offers much needed relief to organizations concerned about preventing Spectre exploits. –– unburdening IT from patching microcode flaws and ensuring a strong defense against future business crippling Spectre variants without an urgency to upgrade systems.
Learn more about Spectre and Meltdown
Read Spectre Will Haunt Us for A Long Time article by Willy Leichter
Download Spectre and Meltdown Attack Prevention white paper