Just before Thanksgiving, the Department of Homeland Security (DHS) released its refreshed list of the 25 Most Common Software Weaknesses.
The list of Common Weakness Enumeration (CWE) contains the 25 most dangerous software errors, so named because they are considered the most frequent and critical errors that can result in the worst software vulnerabilities. DHS manages HSSED – Homeland Security Systems Engineering and Development Institute (HSSED), operated by MITRE, released an updated top 25 CWE list just a couple months ago for the first time in eight years. (See our blog Memory Errors Top MITRE’s ‘Most Dangerous’ List).
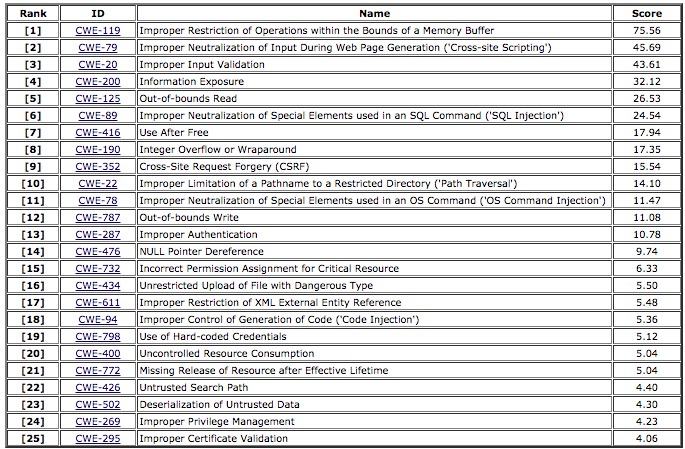
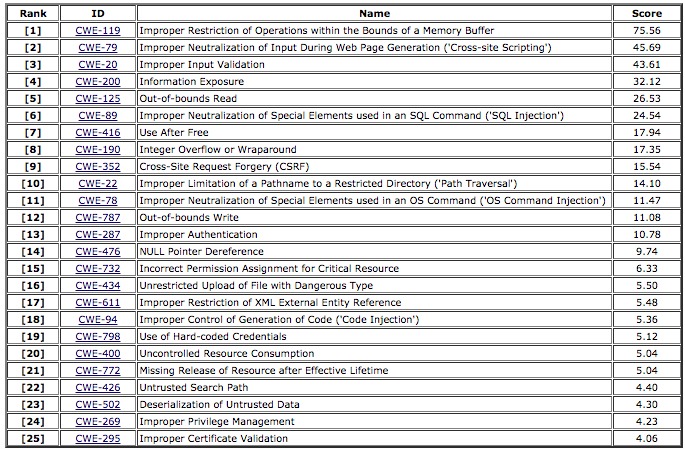
2019 CWE Top 25 Most Dangerous Software Errors
The Top 25 CWE list typically allows threat actors to take control of software, either by altering or stopping its execution or by stealing data. The CWE Top 25 is available as a community resource to help developers in the software industry be informed and defensive in their efforts to combat software threats.
The CWE Team uses data from the Common Vulnerabilities and Exposures (CVE) list and Common Weaknesses Enumeration (CWE) in the National Vulnerability Database (NVD) and National Institute of Standards and Technology (NIST).
Ray DeMeo, Co-Founder and COO of Virsec
Ray DeMeo says it’s encouraging to see the DHS actively promoting the list of top software vulnerabilities compiled by NIST and MITRE. The biggest take-away is that memory buffer errors top the list with by far the highest risk score. These types of in-memory vulnerabilities are poorly understood, bypass conventional security tools, and are increasingly exploited in major attacks like WannaCry, NotPetrya, Industroyer and many others. While this list is helpful in raising awareness, we still have a long way to go to effectively protect against the most dangerous threats.
Virsec Solutions Equipped to Tackle the MITRE 25
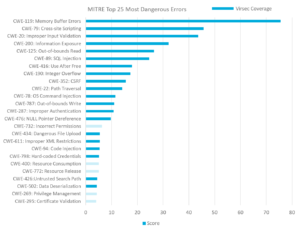
The top 10 errors of the MITRE list account for almost 80% of the total weighted risk and are all related to advanced memory or web threats. Virsec is the only vendor that provides complete protection across the full application stack including the web, memory and host layers. Mapping coverage to the new MITRE list, Virsec provides:
– Complete coverage for MITRE’s top 10 errors
– Coverage for errors that account for 94% of the total risk scores
– Full coverage for all the Memory and Web errors listed, accounting for 92% of the total risk
– Coverage for 20 out of top 25 most dangerous errors listed
Sources:
https://cwe.mitre.org/top25/archive/2019/2019_cwe_top25.html
Further resources:
Top CVE List Analysed by Virsec Lab
Memory Errors Top MITRE’s ‘Most Dangerous’ List https://virsec.com/memory-errors-top-mitres-most-dangerous-list/
Why Companies Need an Application Memory Firewall
Gartner Market Guide Calls Memory Protection a “Mandatory Capability”
The Memory Attack Battleground
MY TAKE: Memory hacking arises as a go-to tactic to carry out deep, persistent incursions