Large Attack Vector - Unpatched Application Workloads
CISOs and IT leaders looking for preventative solutions to the onslaught of nation-state and cybercriminal attacks are extending zero-trust to application workloads to address the gap left by unpatched servers. These extensions often take the form of compensating or mitigating security controls to enhance their existing framework.
One of the principles of Zero Trust is to go beyond the perimeter and defend inside the organization as if a breach has already occurred. Within this layered approach, Virsec addresses server workloads specifically. Many vendors define ‘endpoints’ with the same characteristics, whether a mobile device, laptop, or email server. Virsec’s approach is the opposite. We view the server as having unique attributes, such as restricted access. Applications on a server are vetted, accessed from a more static location, and users have a many-to-one relationship to the server.
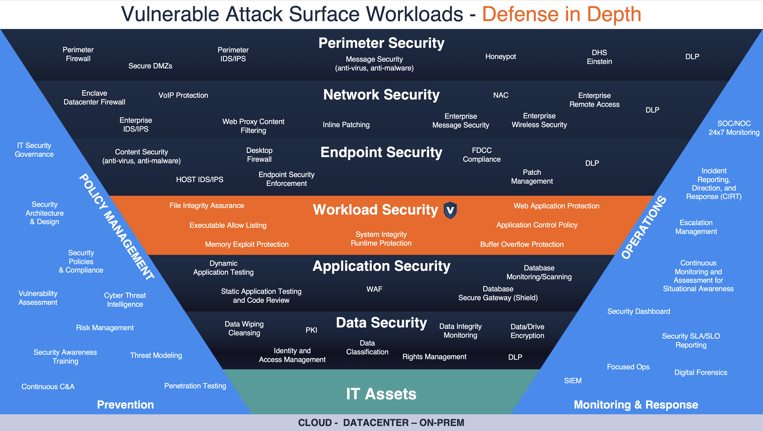
Zero Trust Protection for Application Workloads
One open attack surface that is causing major damage to businesses and organizations globally is legacy, out-of-extended-support application workloads. As Jai Vijayan Contributing Writer, Dark Reading wrote in his article “Most Q2 Attacks Targeted Old Microsoft Vulnerabilities”, “The most heavily targeted flaw last quarter was a remote code execution vulnerability in Microsoft Office that was disclosed and patched four years ago.”
Many business reasons justify a legacy application still being needed. In some cases, that application came with an acquisition ten years ago, but now the whole company uses it. In other cases, it’s a home-grown client-server application with few IT people around anymore that know how it works, and migrating is too expensive.
The challenge is, with or without Extended Support or Extended Security Updates (ESU), security patches are very expensive and leave you exposed to existing vulnerabilities until the custom patch is received, tested, and deployed. With fees more than the price for the original license investment, there has to be a better solution. Virsec’s positive security posture delivers zero-trust, deterministic protection for legacy systems (such as Windows 2003, 2008, 2012, and RHEL / CentOS Linux 6, 7) and addresses, host, and OS open attack vectors with proactive workload protection.
The rest of this blog will describe how and what Virsec does to apply zero trust protection to Microsoft legacy Host OS workloads continue reading to learn how to close the door to this open attack surface.
The Need for Zero Trust Protection
Many IT and DevSecOps organizations have chosen the path laid out by zero-trust principles but have stumbled along the way as the hype and misinformation misformed consumers' expectations. One culprit is applying “detect and response” tactics and techniques which run counter to the very principles of zero trust, such that there is no implicit trust granted. Yet, when we visualize the relative volume of code dependencies, libraries, processes, and files by default, endpoint detection and response (EDR) systems allow all.
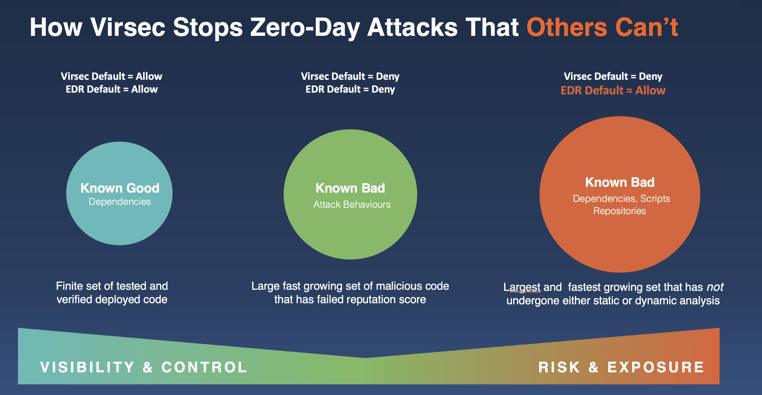
As the Executive Order on Improving the Nation’s Cybersecurity clearly outlines, “The United States faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people’s security and privacy.” This highlights the need for a new approach that applies Zero Trust principles and tactics of a positive security model to open attack surfaces such as legacy host workloads.
The Risk of Unpatched and Legacy Application Workloads
Security priorities can be challenging to prioritize given current resources and growing patch backlogs, but legacy application workloads present a ripe target today and need a solution. Many older vulnerabilities stem from Internet-facing email servers with out-of-support IT applications and services, with unpatchable host operating system (OS) versions, no or limited access to security patches, and few to no skilled team members that could confidently make any meaningful changes.
The Top 15 Routinely Exploited Vulnerabilities in 2021 coauthored by cybersecurity authorities of the United States, Australia, Canada, New Zealand, and the United Kingdom, highlight three significant repeating patterns by malicious cybercriminals:
- Targeting Internet-facing systems, such as email servers with exploits of newly disclosed vulnerabilities - unpatched systems
- Exploitation of publicly known, dated software vulnerabilities
- Nine out of the top 10 vulnerabilities were Remote Code Execution (RCE) or arbitrary code execution in 2020, and eight of 10 in 2021
The first pattern is reinforced later in this blog with data on the types of application servers being targeted. But please note the impact of unpatched security updates is a growing trend that highlights the need for a different approach. To learn more about Virsec’s Zero Trust approach to solving the challenge of Overcoming Patching Pitfalls, please review the highlighted blog.
Preferred Attack Surface: Web and Mail Servers
From Verizon’s Data Breach Investigations Report (DBIR) 2022 below, web applications and mail servers are the prime targets as they present an Internet-accessible access point to deliver the largest impact for ransomware or malware attacks.
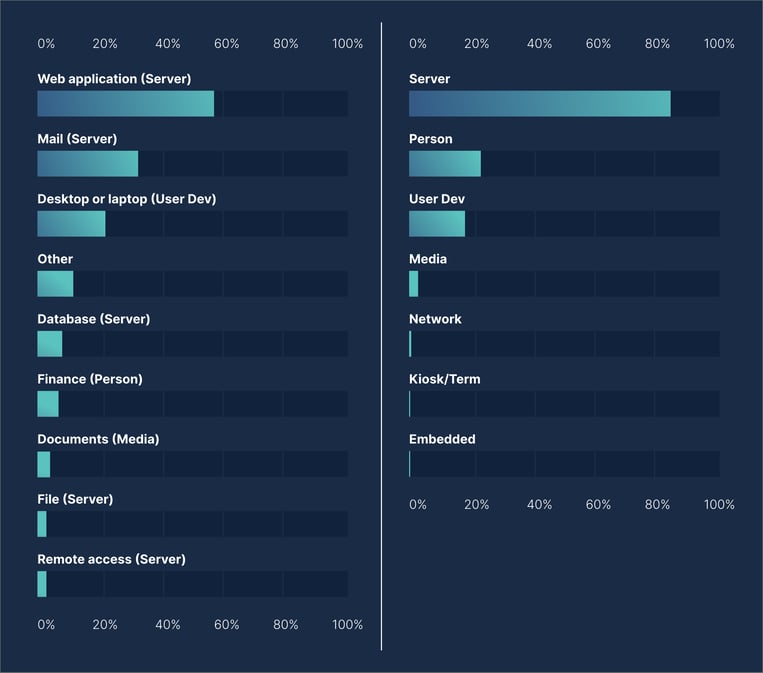
The second pattern is equally alarming and is the focus of this blog, as “75% of attacks in 2020 used vulnerabilities that were at least two years old” and “three out of four attacks took advantage of flaws that were reported in 2017 or earlier. And 18 percent of attacks utilized vulnerabilities that were disclosed in 2013 or before, making them at least seven years old.” Legacy systems represent a high-risk attack surface that can be timely and resource-intensive to close. With recent Virsec feature enhancement, legacy OS workloads such as Windows 2003, 2008, and RedHat and CentOS Linux 6.5, 7, and 8 can now have host-level protection against these growing risks.
Attack Vector: Non-Patchable Windows Servers
One attack vector that has drawn recent visibility is the growing risk associated with legacy server workloads, particularly end-of-life and end-of-extended lifecycle support for Windows 2003 and CentOS and RHEL Linux 6 servers. For organizations that are asking, “After Microsoft assisted and paid support offerings have ended, what are my options?”, Microsoft offers:
Once a product transitions out of Extended Support, no further support will be provided unless an Extended Security Update (ESU) program is available for that product. If ESUs are not offered, customers will not have access to the following:
- Security updates
- Free or paid assisted support options
- Microsoft product development resources
- Updates to online content (Knowledge Base articles, etc.)
- Online content may be available if the product is still within the Self-Help Support phase.”
Without direct support for maintenance or security patches, regulated industries such as; healthcare, financial, and public sector IT organizations are left with few options to adhere to regulatory policies and procedures.
The third pattern is at the core of what Virsec delivers – zero trust deterministic protection by leveraging the patented Virsec Map technology to protect high-value enterprise workloads from increasingly sophisticated cyber-criminal attacks, including; memory corruption, code injection, supply chain poisoning, web attacks, and others.
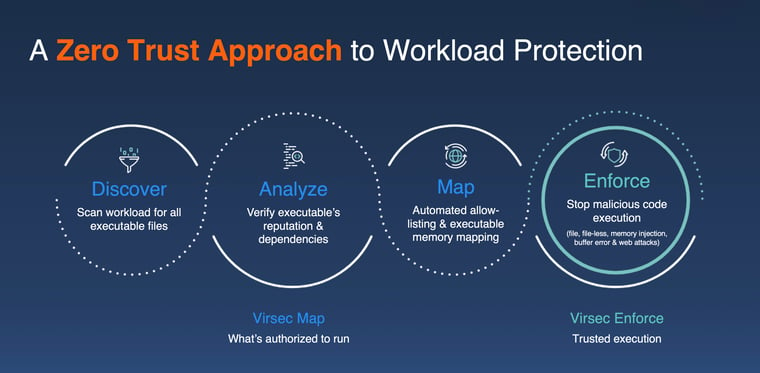
Unlike behavioral-based approaches that “estimate” malicious patterns, Virsec Security Platform takes a positive security posture to deliver a deterministic approach to authorize dependencies with certainty for runtime execution. Virsec Enforce automatically delineates between authorized dependencies such as files, scripts, and libraries from the Software Bill of Materials (SBOM) and instantly stops any unauthorized exceptions.
Enforcement via Compensating Security Controls
One option is based on the National Institute of Standards and Technology (NIST) Special Publication 800-53 Revision 5 covering ‘Security and Privacy Controls for Information Systems and Organizations’. Virsec Security Platform delivers compensating controls for system and information integrity and application workload protection to enhance the defense in depth security strategies for legacy environments.
The Virsec Security Platform (VSP) replaces implicit trust with explicit trust (deny-all until proven to be authorized) to optimize the security posture for legacy workloads. VSP leverages the patented Virsec Map technology to protect application and host workloads from modern Remote Code Execution (RCE) and other sophisticated attacks, including memory corruption, code injection, supply chain poisoning, web attacks, and several others.
Virsec takes the guesswork of ‘what’s running' out of the equation. Furthermore, unlike detect and respond solutions aiming to secure server workloads, Virsec protects in near real-time, delivering zero dwell time coverage until a patch can be made. The positive impact is, should an attack happen, there is no need to quarantine and take the host offline, VSP takes a positive security posture to deliver a deterministic approach, and Virsec Enforce automatically delineates between authorized dependencies such as files, scripts, and libraries and instantly stops any deviations.
Windows 2003 SP2 Compensating Security Control - Virsec
With the latest release of the Virsec Security Platform, IT organizations now have a solution to address the legacy workload attack surface and reduce the risk and resources required to protect their data and IT server assets. The release adds support for Windows 2003 SP2 in both 32-bit and 64-bit, including these editions:
- Windows Server 2003 with SP2(32 bit)
- Windows Server 2003 with SP2(64 bit)
One of the main security capabilities of the Virsec Security Platform (VSP) that provides provenance, integrity, and authorization is the ability to trust files based on the authorized publisher. For Windows 2003, the list of Trusted Root Certificates identifies the source of trust, allowing Virsec to know that it follows the proper root certifications and verifies that the server has a publisher. Once the publisher is part of the Virsec allow-list, any new file in the future signed by that publisher is automatically allow-listed for ease of operations.
Summary
There is an increasing number of articles detailing Microsoft Server Workloads as a prime target for cybercriminals. Keeping legacy Windows and Linux servers under-served with little to no patching, little to no maintenance, and a growing threat profile is a problem that can be avoided with the Virsec Security Platform today.





