NSA EternalBlue, DoublePulsar Hacking Tools Stolen in 2016, Leaked into the Wild in 2016 and 2017
A Chinese state-sponsored group has been using the infamous hacking tools - EternalBlue, DoublePulsar - and variants, for years now. Apparently, even before they were stolen and released by The Shadow Brokers.
These dangerous hacking tools have some history. In August of 2016, the mysterious group called The Shadow Brokers released its first round of stolen NSA hacking tools into the wild. They reportedly stole these prized hacking tools from the Equation Group, the NSA’s own private hacking group.
The second leak from the Shadow Brokers came in October 2016, followed by the third in December and two more in April of 2017. Soon after the final Shadow Broker leaks in April 2017, the stolen hacking tools (DoublePulsar, EternalBlue, EternalRomance), were used to carry out two of the world’s most destructive cyberattacks to date – WannaCry and NotPetya. Both wreaked havoc on organizations and systems globally and costing into the billions in damage. These two cyberattacks are still thought to be the most destructive malware attacks to date. They were also thought to be the first instance of these stolen NSA hacking tools being used. But they may not have been the first.
DoublePulsar, EternalBlue and EternalRomance exploits repeatedly used
The initial theft of the Equation Group hacking tools was an extraordinary feat, and the subsequent release of the hacking tools to the general public stunned the cybersecurity world and brought controversy and embarrassment to the NSA. Not to mention a lot of grief and cost to many organizations every since who’ve been facing a new level of malware attacks. The Equation Group is considered elite among espionage experts and its collection of hacking tools can only be described as a treasure beyond measure.
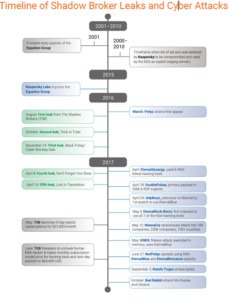
Chinese state-sponsored group – 'Buckeye' – used hacking tools before Shadow Broker leaks
Researchers have found evidence that a Chinese state-sponsored hacking group was using the NSA hacking tools (DoublePulsar, etc.), as well as variants of the hacking tools, such as APT3 and Gotchic Panda, up to a year prior to the Shadow Broker leaks.
This raises questions about whether a different band of thieves robbed the NSA ahead of the Shadow Brokers infamous breach, about which the NSA has already faced difficult questions over how their security could have been breached so drastically – possibly twice. The theft of these hacking tools – arguably among its most valuable assets ever - is possibly the most regrettable and damaging events in their history, both to its own reputation as well as to the security of organizations worldwide.
Research firms have agreed that the Chinese-sponsored group is a Chinese Ministry of State Security contractor operating out of Guangzhou. Buckeye is the nickname Symantec has given this group, and another is APT3, for Advanced Persistent Threat 3.
Buckeye carried out their attacks with stolen NSA hacking tools in 2016 and also variants of those hacking tools. The origin of these variant hacking tools is uncertain. In March 2016, it appears Buckeye began using the DoublePulsar tool with a Trojan exploit tool, Bemstour, to target computers in Hong Kong. Bemstour achieves remote kernel code execution by exploiting two Windows vulnerabilities:
1) CVE-2019-0703 - a zero-day vulnerability discovered by Symantec
2) CVE-2017-0143 – uses EternalRomance and EternalSynergy, two exploit hacking tools released by the Shadow Brokers.
Microsoft patched the exploit in March 2017 after Symantec found the leak.
How did the Buckeye Group get the Equation Group’s hacking tools?
Given these attacks predate the 2017 leaks from the Shadow Brokers, it begs the question of how did the Buckeye group get the hacking tools ahead of when they were leaked into the wild? Evidently, the Equation Group or NSA was breached prior to the Shadow Brokers were known to have done so.
It was already known that a mysterious unknown party stole disks of secret information from the NSA in 2013. It appears they (or he/she) sat on this information for three years before releasing the information, a detail which raises a lot of questions. Who was that entity and did they provide the hacking tools to the Buckeye group? If it was the Shadow Brokers, why did they allow three years to pass before identifyhing themselves and officially releasing the stolen hacking tools?
While Buckeye used the hacking tools in 2016, researchers don’t believe the group is responsible for stealing them. Researchers believe they took the hacking tools and repurposed them for their own use. Even though the Buckeye group seems to have disappeared in 2017, the variant hacking tools are still being used.
Researchers wrote, “Based on the timing of the attacks and the features of the hacking tools and how they are constructed, one possibility is that Buckeye may have engineered its own version of the hacking tools from artifacts found in captured network traffic, possibly from observing an Equation Group attack.”
Ray DeMeo, Co-founder and COO of Virsec, told Security Ledger:
“The idea of stockpiling cyberweapons is problematic. Unlike conventional weapons, most cyber weapons exploit long-dormant vulnerabilities in widely used applications and platforms like Microsoft Windows. Keeping a widespread vulnerability secret and hoping that no other players discover it is inherently dangerous. Plus, if using a new cyber weapon allows your adversary to grab it, improve upon it, and turn it against you then we should be thinking a lot more about defense, rather than risky offensive moves.
However these hacking tools got out there, we’ve now entered a new level in the cyber arms race where hacking tools like Double Pulsar and Eternal Synergy exploit a blind spot in cybersecurity, attacking applications during runtime at the memory level. It’s imperative that we deploy new defenses against these fileless attack that easily bypass conventional security.”
Further resources:
White paper: How The Shadow Brokers Have Permanently Changed The Cybersecurity Landscape
Newsletter: Latest issue
Web Application Security: Product page
Blog: Prediction Series #9: Hackers continue spending weeks & months of dwell time in networks
Sources:
https://securityledger.com/2019/05/chinese-apt-group-used-stolen-nsa-hacking-hacking tools-before-shadow-brokers/
https://www.symantec.com/blogs/threat-intelligence/buckeye-windows-zero-day-exploit
https://www.nytimes.com/2019/05/06/us/politics/china-hacking-cyber.html


